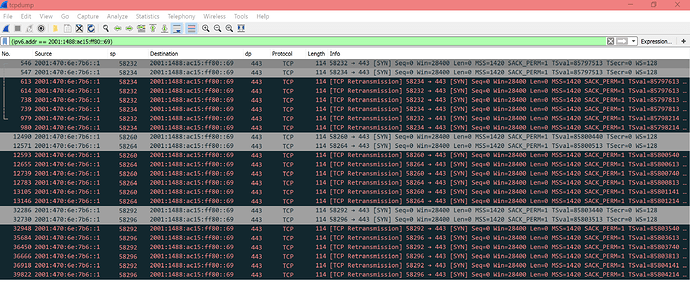
I’ve tried this:
root@turris:~# tcpdump -i eth1 |grep 2001:1488:ac15:ff80::69
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
18:42:40.109413 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842 > 2001:1488:ac15:ff80::69.443: Flags [.], ack 3458442267, win 501, options [nop,nop,TS val 2226227312 ecr 159683456], length 0
18:42:40.127826 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842: Flags [.], ack 1, win 551, options [nop,nop,TS val 159686016 ecr 2226206952], length 0
18:42:40.991959 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 tunnel306502.tunnel.tserv27.prg1.ipv6.he.net.57590 > 2001:1488:ac15:ff80::69.443: Flags [S], seq 4047493447, win 28400, options [mss 1420,sackOK,TS val 85724247 ecr 0,nop,wscale 7], length 0
18:42:41.983856 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 tunnel306502.tunnel.tserv27.prg1.ipv6.he.net.57590 > 2001:1488:ac15:ff80::69.443: Flags [S], seq 4047493447, win 28400, options [mss 1420,sackOK,TS val 85724347 ecr 0,nop,wscale 7], length 0
18:42:42.157423 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33870 > 2001:1488:ac15:ff80::69.443: Flags [.], ack 1315294399, win 501, options [nop,nop,TS val 2226229360 ecr 159683952], length 0
18:42:42.158365 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33730 > 2001:1488:ac15:ff80::69.443: Flags [.], ack 714959533, win 1362, options [nop,nop,TS val 2226229361 ecr 159683933], length 0
18:42:42.165130 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33870: Flags [.], ack 1, win 273, options [nop,nop,TS val 159686528 ecr 2226208996], length 0
18:42:42.166111 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33730: Flags [.], ack 1, win 1439, options [nop,nop,TS val 159686528 ecr 2226218978], length 0
18:42:43.983808 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 tunnel306502.tunnel.tserv27.prg1.ipv6.he.net.57590 > 2001:1488:ac15:ff80::69.443: Flags [S], seq 4047493447, win 28400, options [mss 1420,sackOK,TS val 85724547 ecr 0,nop,wscale 7], length 0
18:42:44.856843 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842 > 2001:1488:ac15:ff80::69.443: Flags [.], seq 1:1409, ack 1, win 501, options [nop,nop,TS val 2226232059 ecr 159686016], length 1408
18:42:44.856873 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842 > 2001:1488:ac15:ff80::69.443: Flags [P.], seq 1409:1539, ack 1, win 501, options [nop,nop,TS val 2226232059 ecr 159686016], length 130
18:42:44.875392 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842: Flags [.], ack 1539, win 575, options [nop,nop,TS val 159687203 ecr 2226232059], length 0
18:42:44.884023 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842: Flags [P.], seq 1:794, ack 1539, win 575, options [nop,nop,TS val 159687205 ecr 2226232059], length 793
18:42:44.885078 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842 > 2001:1488:ac15:ff80::69.443: Flags [.], ack 794, win 495, options [nop,nop,TS val 2226232088 ecr 159687205], length 0
18:43:03.297115 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842 > 2001:1488:ac15:ff80::69.443: Flags [.], seq 1539:2947, ack 794, win 501, options [nop,nop,TS val 2226250500 ecr 159689729], length 1408
18:43:03.297146 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33842 > 2001:1488:ac15:ff80::69.443: Flags [P.], seq 2947:3053, ack 794, win 501, options [nop,nop,TS val 2226250500 ecr 159689729], length 106
18:43:27.726009 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33870 > 2001:1488:ac15:ff80::69.443: Flags [.], ack 1171, win 501, options [nop,nop,TS val 2226274928 ecr 159695403], length 0
18:43:27.733729 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33870: Flags [.], ack 2985, win 319, options [nop,nop,TS val 159697920 ecr 2226264867], length 0
18:44:22.510615 IP 188-175-41-253.client.rionet.cz > tserv1.prg1.he.net: IP6 2001:470:6e:7b6:fef8:aeff:fe36:218a.33730 > 2001:1488:ac15:ff80::69.443: Flags [.], ack 2756, win 1362, options [nop,nop,TS val 2226329712 ecr 159709095], length 0
18:44:22.518324 IP tserv1.prg1.he.net > 188-175-41-253.client.rionet.cz: IP6 2001:1488:ac15:ff80::69.443 > 2001:470:6e:7b6:fef8:aeff:fe36:218a.33730: Flags [.], ack 8076, win 1439, options [nop,nop,TS val 159711616 ecr 2226319627], length 0
On second session I’ve started the wget command above. The last two rows were received after wget failed on timeout. I’ve no idea what these rows shows 
Now I’m trying command you posted.