I’m sorry but I don’t understand it yet.
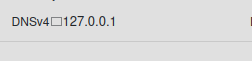
I don’t see 127.0.0.1 anywhere like you do.
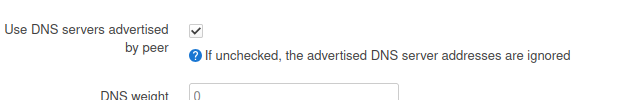
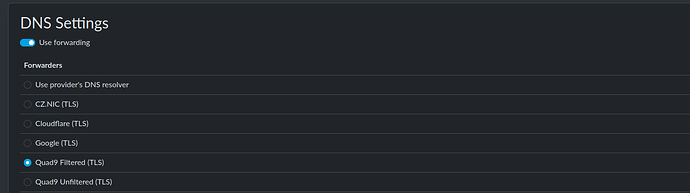
What I do in reForis is to set the Quad9 server in “DNS”.
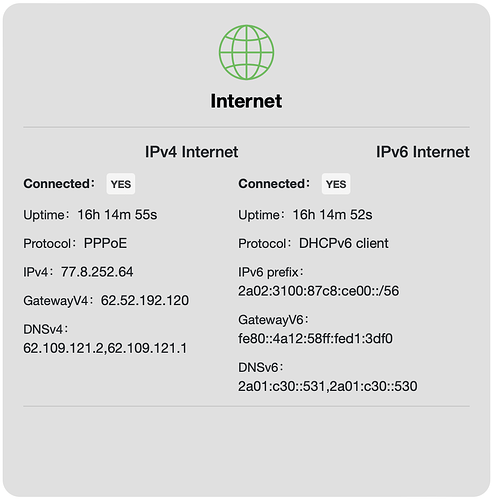
If I leave everything in Luci as it is by default, then my /etc/resolv.conf contains the DNS server from the ISP.
cat /etc/resolv.conf
# Interface wan
nameserver 217.5.100.185
nameserver 217.5.100.186
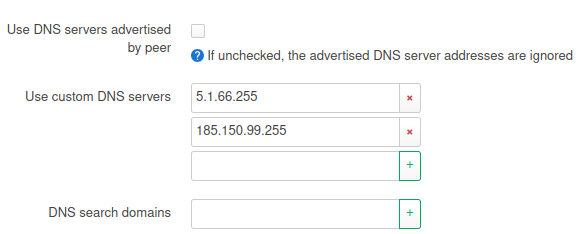
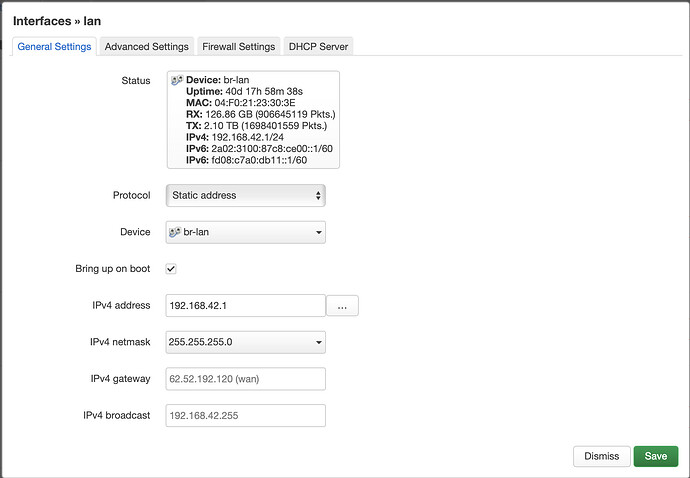
I then enter my custom DNS in Luci on the WAN interface as described above:
Then exactly these servers are listed in
/etc/resolv.conf.
cat /etc/resolv.conf
# Interface wan
nameserver 5.1.66.255
nameserver 185.150.99.255
Here is my dig output:
dig www.heise.de | grep SERVER
;; SERVER: 5.1.66.255#53(5.1.66.255) (UDP)
Here with trace option, I can also found my custom DNS server there:
dig www.heise.de +trace
; <<>> DiG 9.18.24 <<>> www.heise.de +trace
;; global options: +cmd
. 14404 IN NS e.root-servers.net.
. 14404 IN NS a.root-servers.net.
. 14404 IN NS j.root-servers.net.
. 14404 IN NS g.root-servers.net.
. 14404 IN NS l.root-servers.net.
. 14404 IN NS c.root-servers.net.
. 14404 IN NS k.root-servers.net.
. 14404 IN NS b.root-servers.net.
. 14404 IN NS i.root-servers.net.
. 14404 IN NS d.root-servers.net.
. 14404 IN NS h.root-servers.net.
. 14404 IN NS m.root-servers.net.
. 14404 IN NS f.root-servers.net.
. 14404 IN RRSIG NS 8 0 518400 20250123170000 20250110160000 26470 . MuUwkK7YHpJAu4frvRLM+RE7TBiC2RAq5A5f57vMBvdsgxvuWgZZgo3W mIRw+5SFzg0TF8Pj61GhEgXEg/ceiFTp2qZZGwtddk/tfvXr83hAMj4T Qd9Aq8a4KapN8C/OqaQs/L7cEQUyLR4kUmLyZ3A/zkQ3EE8miLlmY15I 2eZEi4w1mLx7t9elPibc9XjEhj0RIR/Fy4nyTXc/DWxT/UHFkez0KpeZ ksQmJBasVGxLSck1cKL8xKzTfp4DM1BJLPi1ItDDRN2p7E5JaoEFfsm3 ri6XDCGugpNlxnXNIPAoiKOoYyqWSApGy3//dhhpHx6JDuWplMO+h8oU Y0luNw==
;; Received 525 bytes from 5.1.66.255#53(5.1.66.255) in 10 ms
de. 172800 IN NS l.de.net.
de. 172800 IN NS z.nic.de.
de. 172800 IN NS a.nic.de.
de. 172800 IN NS f.nic.de.
de. 172800 IN NS s.de.net.
de. 172800 IN NS n.de.net.
de. 86400 IN DS 26755 8 2 F341357809A5954311CCB82ADE114C6C1D724A75C0395137AA397803 5425E78D
de. 86400 IN RRSIG DS 8 1 86400 20250124170000 20250111160000 26470 . CeL5xwb6fS+ktDT97m/0mxKizNSY4zuxn/UDdpsASLOd9NPp6pTMR8et mhu5c8EV5zk0bWdeIaIW6iP1FKLj+tGgwSkvp1KqIspMp7IM7jgQFG3s jsO4C8X+rS7oFX2a4XtHkNHpTH6slUhRqhSnw1pYjI/GabEGiaREWoLg 0TwrUKkWKSSOWoiPvRP5nNZVd24dvc2+nqts85ik3svWb7g4aGTWfLbJ OsHLxk5liUln3vkbmdTNDxEr87kYX908RoH1GHdhU3d7Ugt5HG4tpP68 i5Bp2IFb4lw3Q85gf/PaSUqfnjKmFDipzQSWJ7d3UMS04S+lc91ow7S7 sJXK1Q==
;; Received 778 bytes from 192.5.5.241#53(f.root-servers.net) in 0 ms
heise.de. 86400 IN NS ns2.pop-hannover.net.
heise.de. 86400 IN NS ns.pop-hannover.de.
heise.de. 86400 IN NS ns.s.plusline.de.
heise.de. 86400 IN NS ns.heise.de.
heise.de. 86400 IN NS ns.plusline.de.
tjlb7qbojvmlf1s6gdriru7vsms1lg16.de. 7200 IN NSEC3 1 1 15 CA12B74ADB90591A TJLCSJAT4LJTVO0TJNCRRDF6KF6ONEFB NS SOA RRSIG DNSKEY NSEC3PARAM
tjlb7qbojvmlf1s6gdriru7vsms1lg16.de. 7200 IN RRSIG NSEC3 8 2 7200 20250122104255 20250108091255 63483 de. Di3Ng8BJ9GKixVJgxwMlJgsCLay/13GxMj4bjr1i8S0e21A7iTaa/TXG QCPNnHJXXPbncRIXkCENtri998s5zw3BvDrY0EcZbCbhigP35nJE4z59 LVUrPu0MoFfamCDwd/6hHcC6X3xx1NgaPKI81myQHaUuYiMkoCDKMH25 roQ=
ga624qcvfdcrth24fblomo7j82lsvu0v.de. 7200 IN NSEC3 1 1 15 CA12B74ADB90591A GA6325GEF7724RVDDS4A1DV460UM3GEE A RRSIG
ga624qcvfdcrth24fblomo7j82lsvu0v.de. 7200 IN RRSIG NSEC3 8 2 7200 20250122104255 20250108091255 63483 de. NSSfw+mN2F4Ul9GkL4GmcjJT6DdT6Mfd55j9EBuvSoAn6OKKCaLPa6Gr 1EjnHYRI+Vza6C0U01vMw+ztAi8BScnRdWiNmpGEKRnpWAWSqp96ip/f BgijvoFNKF9IjqKnmcVBr6tseJmvKzIjCVPh6k3YIvq8TaDudgnNjYxO xxM=
;; Received 859 bytes from 194.246.96.1#53(z.nic.de) in 10 ms
www.heise.de. 86400 IN A 193.99.144.85
heise.de. 86400 IN NS ns.pop-hannover.de.
heise.de. 86400 IN NS ns.heise.de.
heise.de. 86400 IN NS ns.plusline.de.
heise.de. 86400 IN NS ns2.pop-hannover.net.
heise.de. 86400 IN NS ns.s.plusline.de.
;; Received 343 bytes from 212.19.48.14#53(ns.plusline.de) in 10 ms
The file /tmp/kresd.custom.conf does not exist for me.
Here is my /tmp/kresd.config:
cat /tmp/kresd.config
--Automatically generated file; DO NOT EDIT
modules = {
'hints > iterate'
, 'policy'
, 'stats'
, predict = { window = 0, period = 0 }
}
hints.use_nodata(true)
policy.add(policy.rpz(policy.DENY, '/etc/kresd/adb_list.overall'))
hints.config('/tmp/kresd/hints.tmp')
net.listen('0.0.0.0', 53, { kind = 'dns' })
net.listen('0.0.0.0', 853, { kind = 'tls' })
net.listen('::', 53, { kind = 'dns' })
net.listen('::', 853, { kind = 'tls' })
trust_anchors.remove('.')
trust_anchors.add_file('/etc/root.keys', true)
net.bufsize(1232)
net.ipv4=true
net.ipv6=false
cache.open(20*MB)
table.insert(policy.special_names, { count = 0, cb = policy.all(
policy.TLS_FORWARD(
{{'9.9.9.9'
,hostname='dns.quad9.net'
,ca_file='/etc/ssl/certs/ca-certificates.crt'
},{'149.112.112.112'
,hostname='dns.quad9.net'
,ca_file='/etc/ssl/certs/ca-certificates.crt'
}}))})
user('kresd','kresd')
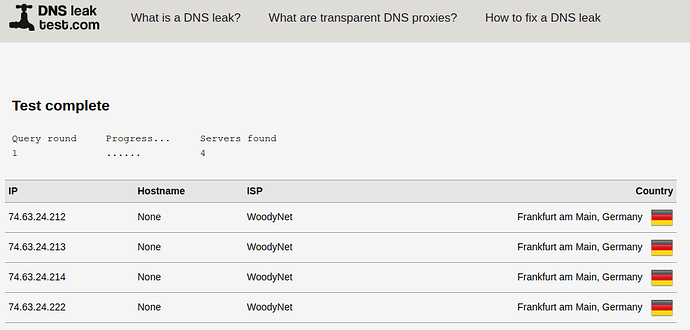
I probably don’t understand it but in the end I have the result I wanted or not? The ISP providers no longer appear anywhere.
It is not yet clear to me whether I should now create the /tmp/kresd.custom.conf myself? Or everything is fine?
Since my dig output or even nslookup shows my custom DNS does it fit then?
nslookup heise.de
Server: 5.1.66.255
Address: 5.1.66.255:53
Non-authoritative answer:
Name: heise.de
Address: 193.99.144.80
Non-authoritative answer:
Name: heise.de
Address: 2a02:2e0:3fe:1001:302::
As I said, I don’t understand everything but would like to learn  and above all I want to be sure that I am not making a configuration error.
and above all I want to be sure that I am not making a configuration error.