Hello all,
I have been happily plugging away on an Omnia running TOS 3. Yesterday and today I attempted to upgrade by doing a fresh install of TOS 6 using @ dhopfm’s awesome post here: The clean path to Turris OS 6 (and any other major version) - SW help - Turris forum. Unfortuently for both days after banging my head against a wall for a few hours each day, I rolledback to the previously working TOS 3.
Background:
My network topology is:
LAN0 -> UniFi Managed Switch (with clients in default vlan 1, 3, and 4)
LAN1 -> UniFi Managed Switch (with clients in default vlan 1, 3, and 4)
LAN2 -> Off
LAN3 -> UnifiAP (with clients in default vlan 1, 3, and 4)
LAN4 -> Off
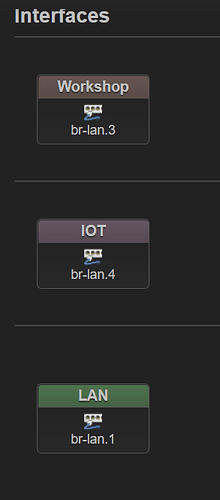
VLAN Nominclature/purpose:
VLAN 1 = Default VLAN
VLAN 3 = Workshop
VLAN 4 = IOT
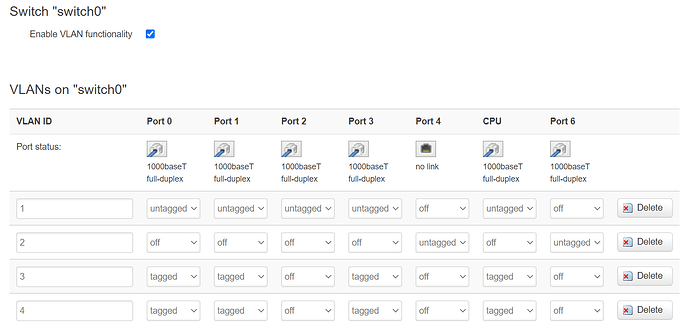
My /etc/config/network and VLAN config on TOS 3:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '{$my_ipv6_prefix}'
config interface 'lan'
option force_link '1'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.12.0.1'
option _orig_ifname 'eth0 eth2 radio0.network1 radio0.network2 radio0.network3'
option _orig_bridge 'true'
option ifname 'eth0 eth2'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
option peerdns '0'
option dns '10.12.0.21'
config interface 'wan6'
option ifname '@wan'
option proto 'dhcpv6'
option noserverunicast '1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0 1 2 3 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '0t 1t 3t 5t'
config interface 'Workshop'
option proto 'static'
option ifname 'eth0.3'
option ipaddr '10.20.30.1'
option netmask '255.255.255.0'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '4'
option ports '0t 1t 3t 5t'
config interface 'IOT'
option proto 'static'
option ifname 'eth0.4'
option ipaddr '10.30.40.1'
option netmask '255.255.255.0'
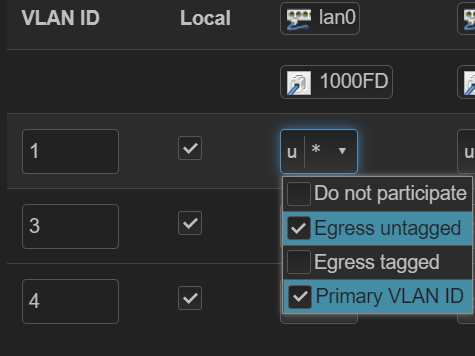
For the visual folks that means my switch config looks like:
I won’t share existing firewall config because it’s sprawling mess but it works.
In preparing for and troubleshooting during the sessions yesterday and today I have read:
- How to make VLAN work again after update from TOS 5 to 6? - SW help - Turris forum
- Mini tutorial for DSA network config - Network and Wireless Configuration - OpenWrt Forum
- and a few other great openwrt posts
…but I am still lost.
In TOS 6 I have so far tried:
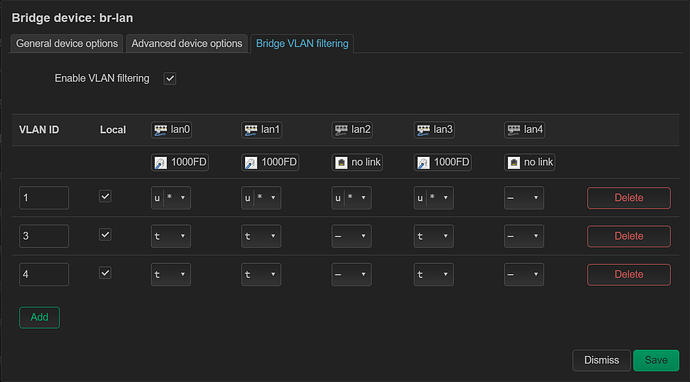
- Enabling VLAN tagging on the default br-lan like was suggested in @hagrid in one of the above posts and translating the untagged/tagged/off to untagged egress / tagged egress / primary VLAN / off for appropriate ports. (Interface → devices → br-lan → Configure → VLAN Tagging)
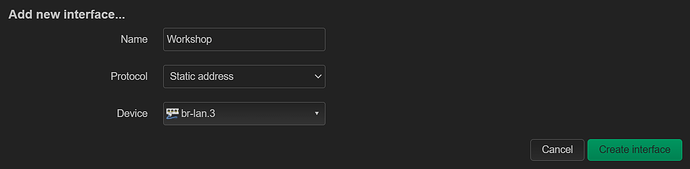
- Creating a Software VLAN hanging off (Interface → devices → New Device → Software VLAN → base-device br-lan)
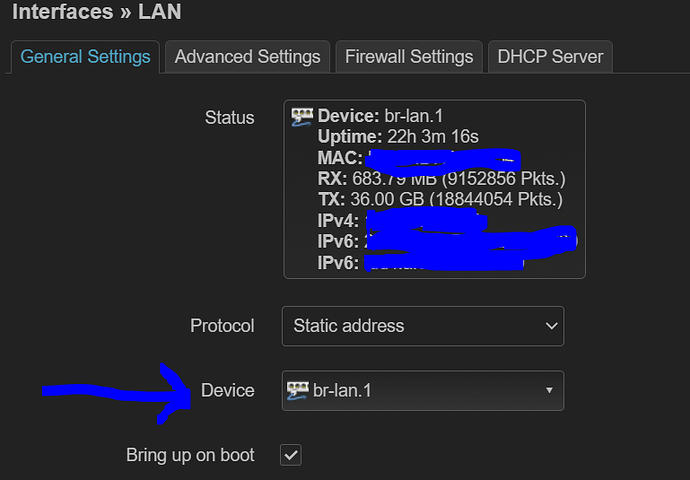
- Creating a new bridge with all LAN ports and recreating the tagging pictured above (minus the VLAN 2)
- Corresponding firewalls were creating for everything to ensure traffic would pass properly.
I’ve been unsuccessful in getting any of the approaches to pass traffic or even see packets. I was careful to only save and not Save & Apply (tho I learned that the hard way crashing my router often).
Asks for community
How can I mimic the above working TOS 3 /etc/network/config in TOS 6 w/ DSA? How can I build out the same VLAN functionality in either the UI or UCI commands?
Any and all help would be hugely appreciated & thanks in advance.