Dear all,
I try to setup a VLAN and I have to admit, I’m completely confused. I read forum posts here and elsewhere on the topic (most notably https://forum.test.turris.cz/t/tos5-vlan-nightmare/13175 and https://forum.test.turris.cz/t/total-obsolete-vlan-documentation/13121) as well as the OpenWRT documentation. I also watched videos on youtube on how to set up VLANs on OpenWRT, which make it appear to be a simple process with Luci - and make me feel even dumber because I can’t get it to work.
I understand that there are differences between different router, of course, and one is not like the other, but it seems I’m unable to transfer the information to my setup.
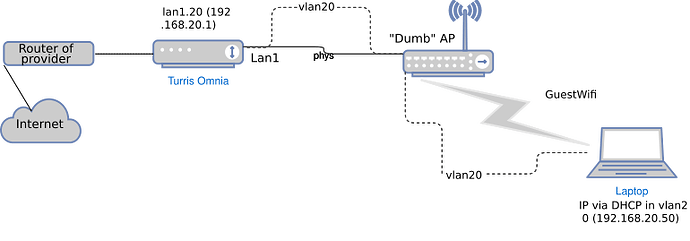
My setup is as follows:
“Dumb” AP is connected to Lan1 port on Omnia. VLAN ID should be 20.
What I try to achieve:
Users connected to the “GuestWifi” should be able to access the Internet, but should not be able to connect devices connected to other networks such as 192.168.1.0/24.
What I did so far:
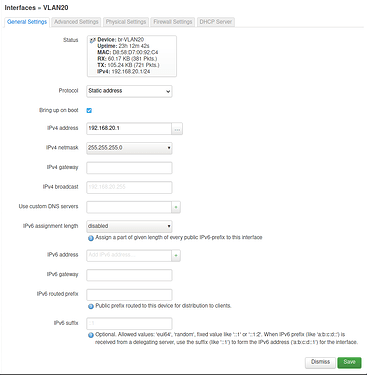
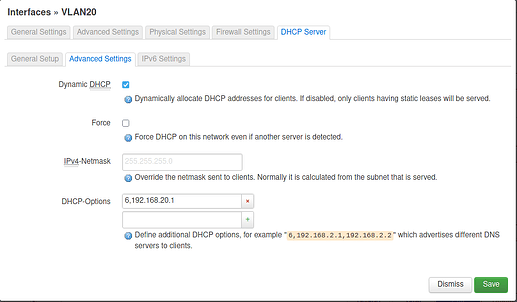
I followed https://docs.turris.cz/basics/luci/vlan/luci-vlan/ to create a virtual interface. In /etc/config/networks it looks like this:
config interface ‘VLAN20’
option proto ‘static’
option ifname ‘lan1.20’
option type ‘bridge’
option netmask ‘255.255.255.0’
option ipaddr ‘192.168.20.1’
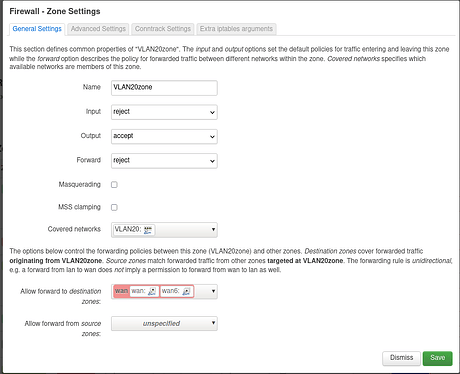
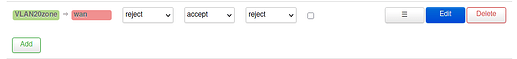
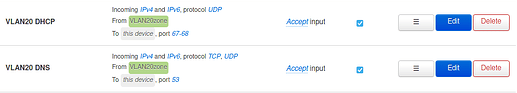
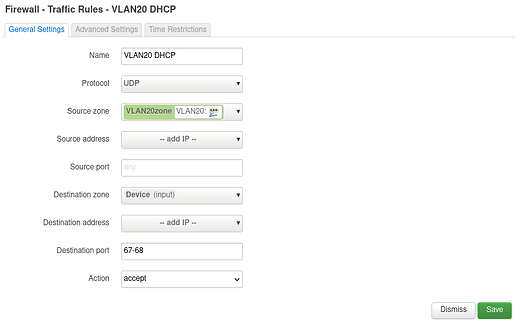
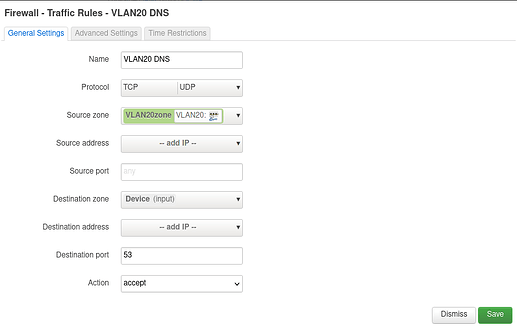
As firewall rules I added:
config zone
option name ‘vlan20forw’
option input ‘ACCEPT’
option forward ‘REJECT’
list network ‘VLAN20’
option output ‘ACCEPT’
config forwarding
option dest ‘wan’
option src ‘vlan20forw’
in /etc/config/girewall using Luci.
What works:
Clients can access GuestWifi.
What does not work:
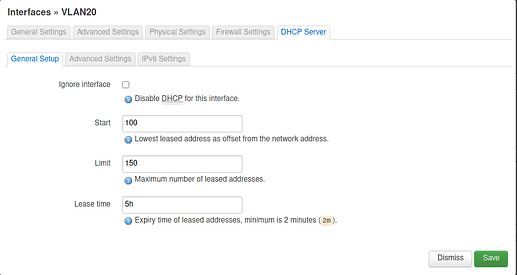
Clients are not assigned an IP address cannot access the Internet.
So, after all this, how do I get it working? Maybe someone has a simple, working configuration to share?
I feel tangled up in information only relevant for TOS3, unclear instructions (or better put instructions I do not understand) and generally content and comments where I can’t determine whether it is still relevant or not.
Every help is highly appreciated! I would also like to help with the documentation on https://docs.turris.cz/basics/luci/vlan/luci-vlan/ to make it into a full Luci-based example.