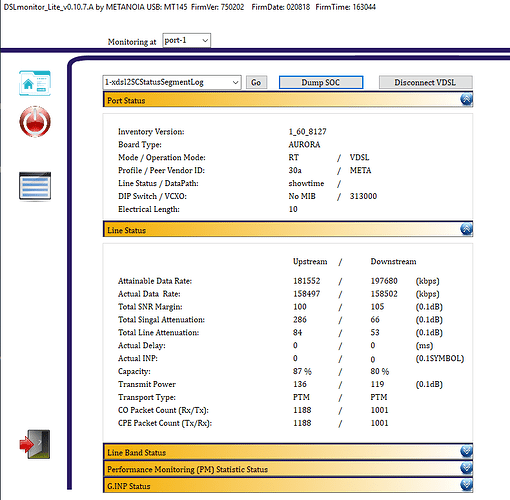
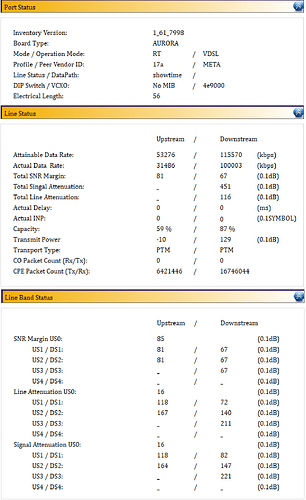
I made a comment on VDSL SFP Bridge Modem - #39 by andre - Turris Omnia - Turris forum
I just bridge the sfp into a management vlan and have the windows box see that)
and @anon50890781 asked me to elaborate.
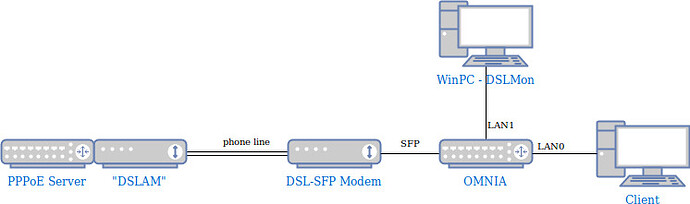
So there an example how I have set it up on an test rig.
First keep in mind what the DSL SFP really is, a DSL modem connected to an ethernet port condensed into an SFP. Therefore to talk to the modem (for stats) you need to address it by using the modem’s MAC address (the one printed on the SFP). If you would use the address of eth1 you would address the Omnia.
In addition note that this is all L2, e.g. no IP/routing involved (the windows box in my example doesn’t have an IP address at all).
Therefore a “simple” bridge will get the result required because a packet with an destination MAC the bridge doesn’t know yet (when the first packet from the Windows box to the modem arrives) will be flooded onto all bridge ports. The bridge will learn where the MAC is when the response from the modem arrives and then send it out the correct port without flooding. (normal switch/bridge principles).
Now to the test setup for illustration.
I started of with an factory reset Omnia with “current” aka 3.11.2.
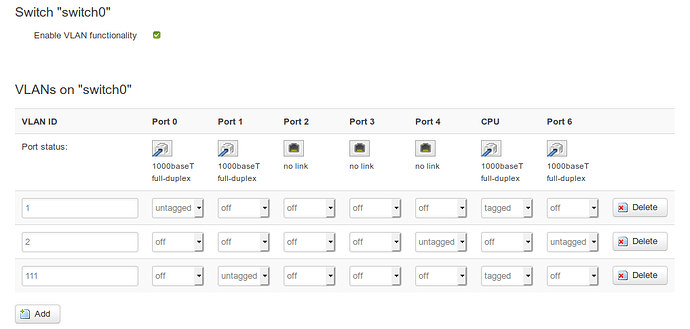
Then I deleted some unnecessary stuff plus reconfigured the switch into tagged mode by:
- enabled VLAN functionality on switch0
- switched the CPU port into tagged mode
- removed all other LAN ports from VLAN 1 but LAN0/Port 0 and CPU (tagged mode)
- replaced eth0 with eth0.1 in the “LAN” interface definition
Note: only “apply” after all the last step or you will lose connectivity
In this way I’m free to use all other ports assigning them to other then the default vlan.
Next I set up the config the the DSL and SFP so that the windows box connected to LAN1 was able to talk to the modem inside the SFP and set up an example PPPoE connection on VLAN 7 via the modem. I picked VLAN 111 as for sfp management.
- added an “SFP” interface as eth1 (SFP port) for visibility, not really required
- changed the “WAN” interface definition to use eth1.7 (VLAN 7 on SFP port) and PPPoE
- created new VLAN 111 on switch0 and added LAN1/Port 1 (the one the windows box is connected to)
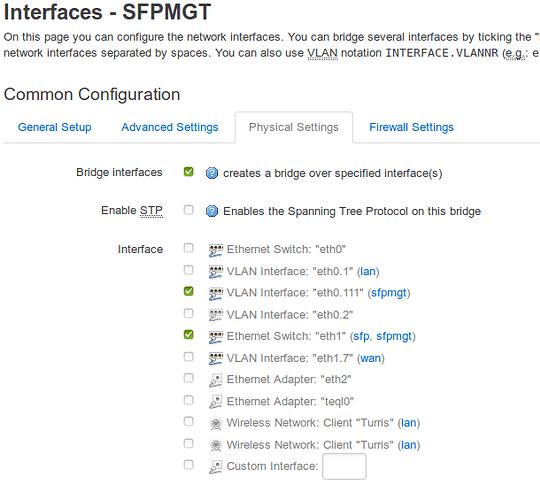
- added an “SFPMGT” network interface bridging eth1 (the SFP port) and eth0.111
Apply and it started working.
Note that the bridge needs to be “up” (ifconfig br-sfpmgt up) or it will not pass traffic. OpenWRT sometimes takes “unmanaged” as meaning not to up the interface. In that case I usually assign an random IP (unused private) to it.
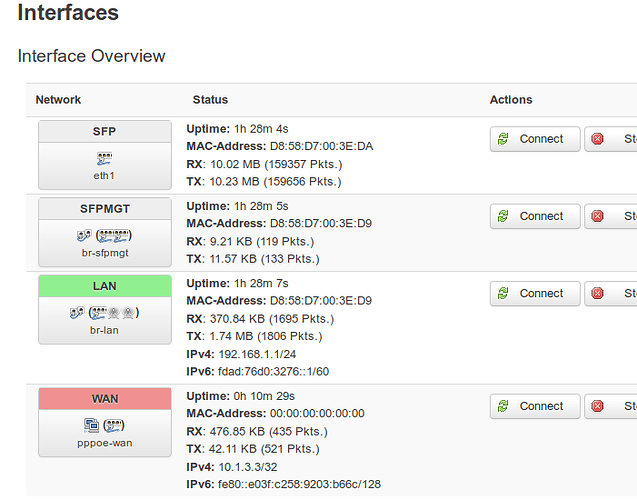
The net result is below
LUCI switch0 config
- Port 0 (on VLAN 1): Client device which can browse the internet via the Omnia
- Port 1 (on VLAN 111): Windows host with the DSLMonitor software running which can only access the modem inside the SFP
- Port 5 (tagged): CPU port between switch and Omnia CPU
- Port 6 (VLAN 2): 2nd CPU port left unchanged
swconfig dev switch0 show output
root@turris:/etc/config# swconfig dev switch0 show
Global attributes:
enable_vlan: 1
Port 0:
mask: 0x0000: (0)
qmode: 3
pvid: 1
link: port:0 link:up speed:1000baseT full-duplex
Port 1:
mask: 0x0000: (1)
qmode: 3
pvid: 111
link: port:1 link:up speed:1000baseT full-duplex
Port 2:
mask: 0x0000: (2)
qmode: 0
pvid: 0
link: port:2 link:down
Port 3:
mask: 0x0000: (3)
qmode: 0
pvid: 0
link: port:3 link:down
Port 4:
mask: 0x0000: (4)
qmode: 3
pvid: 2
link: port:4 link:down
Port 5:
mask: 0x0000: (5)
qmode: 3
pvid: 0
link: port:5 link:up speed:1000baseT full-duplex
Port 6:
mask: 0x0000: (6)
qmode: 3
pvid: 2
link: port:6 link:up speed:1000baseT full-duplex
VLAN 1:
port_based: 0
vid: 1
ports: 0 5t
VLAN 2:
port_based: 0
vid: 2
ports: 4 6
VLAN 3:
port_based: 0
vid: 111
ports: 1 5t
root@turris:/etc/config#
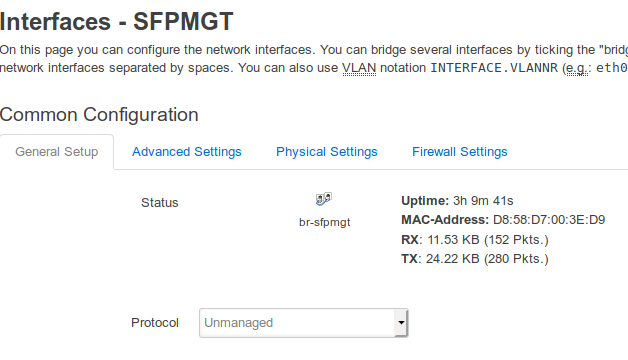
LUCI interface SFPMGT general
/etc/config/network file content
root@turris:/etc/config# cat network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdad:76d0:3276::/48'
config interface 'lan'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option _orig_ifname 'eth0 eth2 radio0.network1 radio1.network1'
option _orig_bridge 'true'
option ifname 'eth0.1'
config interface 'wan'
option _orig_ifname 'eth1'
option _orig_bridge 'false'
option ifname 'eth1.7'
option proto 'pppoe'
option username 'hello'
option password 'world'
option ipv6 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 5t'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '1 5t'
option vid '111'
config interface 'sfp'
option proto 'none'
option ifname 'eth1'
config interface 'sfpmgt'
option ifname 'eth0.111 eth1'
option _orig_ifname 'eth0.111'
option _orig_bridge 'false'
option proto 'none'
option type 'bridge'
root@turris:/etc/config#
Any questions are welcome.
Just a warning, don’t bridge the SFP onto your standard internal network. After all whatever is visible to the modem will be visible to the remote end.