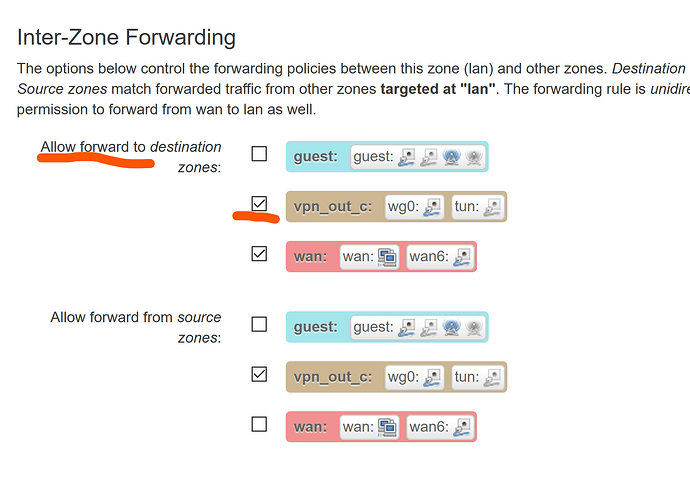
My OpenVPN setup broke a few weeks ago and I’m trying to understand how it all goes together. The actual OpenVPN negotiation works and I can watch ping packets arriving from the remote machine into “tun_turris” however no replies are ever sent. I think this is down to bad routing on the TO side. As I was trying to figure out what’s going on I found there was a br-vpn-turris bridge but it didn’t have the tun_turris device attached.
I’ve deleted everything and want to re-build the config again but I’m confused as to if I need a bridge just for the VPN? Surely I just need the VPN end point and the appropriate routing/forwarding setup? Or should all “zones” be represented by a bridge with one or more interfaces attached to it?
The other option would be to bridge the OpenVPN directly onto my lan but then I think I run into problems of where IP addresses are assigned. Are there any network diagrams of how OpenVPN is meant to integrate with the rest of the system?
Thanks,