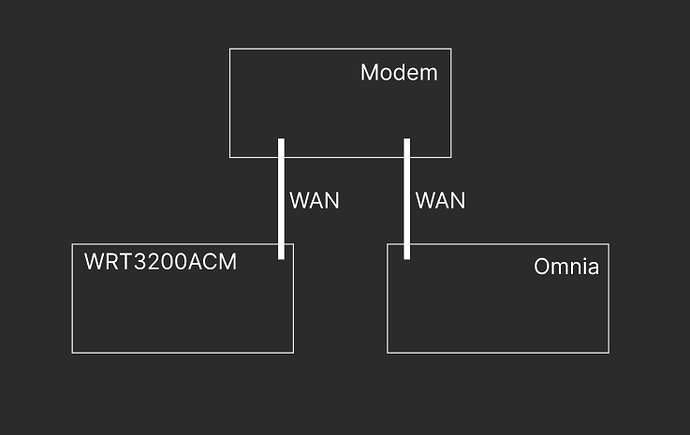
I have Linksys WRT3200ACM [192.168.21.1] with OpenWrt 22.03.2 & Turris Omnia on TurrisOS 6.2.3
Both are connected to a Local Modem (it has couple wan ports) and work as expected apart from wireguard sadly. It works on WRT but not on Omnia
I’ve replicated the setup from WRT to Omnia (with new keys and a different listening port).
I spend days on this and can’t figure out what’s going on, either replicating the same error or Omnia firewall needs some additional tweaking.
This is latest setup after restoring Omnia to defaults and starting over
basically never managed to get a handshake (monitoring using wireguard status in luci)
no problems on WRT (as mentioned before)
please find configs below:
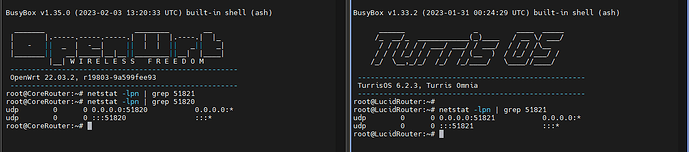
wg show
root@turris:~# wg show
interface: wg0
public key: ogqx[reducted]DEizi0=
private key: (hidden)
listening port: 51821
peer: vZIO[reducted]TCJDA=
endpoint: [reducted]:51821
allowed ips: 10.200.200.2/32
transfer: 0 B received, 14.02 KiB sent
persistent keepalive: every 25 seconds
network
root@turris:/etc/config# cat network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd10:630a:da1a::/48'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ip6assign '60'
option _turris_mode 'managed'
list ipaddr '192.168.2.1/24'
config interface 'wan'
option device 'eth2'
option proto 'dhcp'
option ipv6 '1'
config interface 'guest_turris'
option enabled '1'
option proto 'static'
option device 'br-guest-turris'
option ipaddr '10.111.222.1'
option netmask '255.255.255.0'
option ip6assign '64'
config device 'br_guest_turris'
option name 'br-guest-turris'
option type 'bridge'
option bridge_empty '1'
config device 'br_lan'
option name 'br-lan'
option type 'bridge'
list ports 'lan0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config device 'dev_wan'
option name 'eth2'
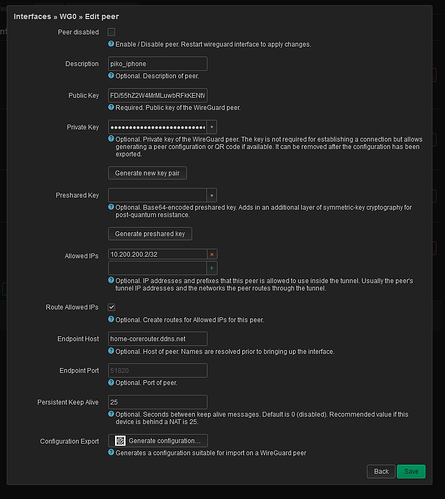
config interface 'wg0'
option proto 'wireguard'
option private_key 'iBhpKRI6HiFeSs38c/N9PcLJ3dMzNv8x3ylGjBSWDn8='
option listen_port '51821'
list addresses '10.200.200.1/24'
config wireguard_wg0
option public_key 'vZIOezAXrtbUvm2tepCGs5UWtxBR2BZVNu878UTCJDA='
option description 'iphone'
option persistent_keepalive '25'
option route_allowed_ips '1'
option endpoint_host '[DDNS-reducted]'
list allowed_ips '10.200.200.2/32'
option endpoint_port '51821'
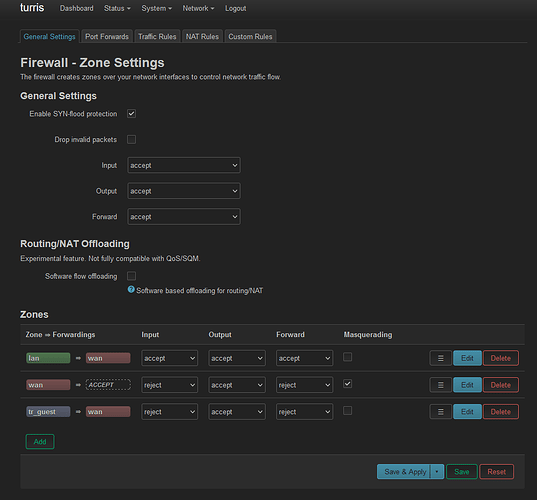
firewall:
root@turris:/etc/config# cat firewall
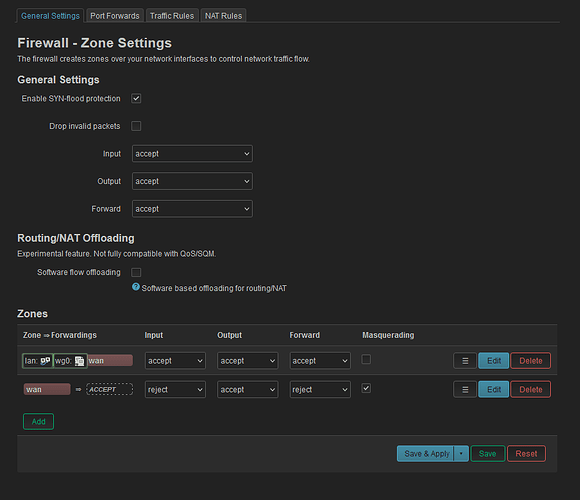
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
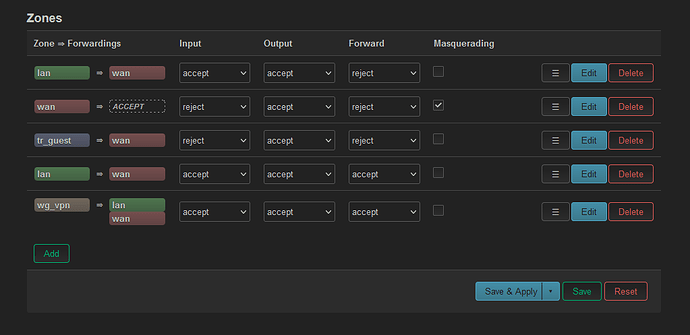
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config zone 'guest_turris'
option enabled '1'
option name 'tr_guest'
list network 'guest_turris'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
config forwarding 'guest_turris_forward_wan'
option enabled '1'
option name 'guest to wan forward'
option src 'tr_guest'
option dest 'wan'
config rule 'guest_turris_dns_rule'
option name 'guest dns rule'
option src 'tr_guest'
option proto 'tcpudp'
option dest_port '53'
option target 'ACCEPT'
config rule 'guest_turris_dhcp_rule'
option name 'guest dhcp rule'
option src 'tr_guest'
option proto 'udp'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
config rule 'guest_turris_Allow_DHCPv6'
option src 'tr_guest'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '546-547'
option dest_ip 'fe80::/10'
option dest_port '546-547'
option family 'ipv6'
option target 'ACCEPT'
config rule 'guest_turris_Allow_MLD'
option src 'tr_guest'
option proto 'icmp'
option src_ip 'fe80::/10'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
config rule 'guest_turris_Allow_ICMPv6_Input'
option src 'tr_guest'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
config rule 'wan_ssh_turris_rule'
option name 'wan_ssh_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '22'
option proto 'tcp'
option src 'wan'
config rule 'wan_http_turris_rule'
option name 'wan_http_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '80'
option proto 'tcp'
option src 'wan'
config rule 'wan_https_turris_rule'
option name 'wan_https_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '443'
option proto 'tcp'
option src 'wan'
config rule 'turris_wan_6in4_rule'
option enabled '0'
config rule 'turris_wan_6to4_rule'
option enabled '0'
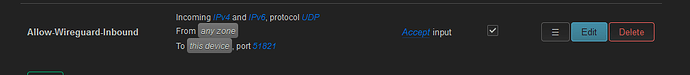
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option name 'Allow-Wireguard-Inbound'
option dest_port '51821'