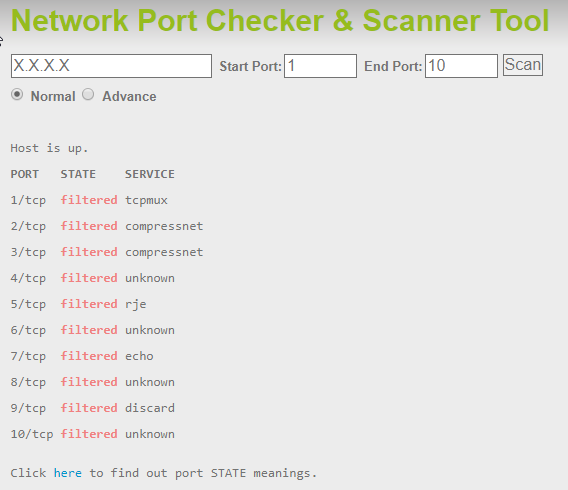
Hello, even though i have a firewall rule to drop the new incoming packets from outside wan, and ping rule disabled, when i run the GRC shields up it shows port 1 (TCP Mux) to be blocked only (not stealth).
Why is it showing port 1 to be blocked, while others are stealth.
Long story:
i was just installing internet to flat after restoration and i chosen the Omnia router (instead an older cisco 7301 which was there previously as this flat will not longer be joined to my DMVPN), and when i ran the GRC Shields Up it showed all ports are blocked(blue) (not stealth…) and ping was allowed. so i went to luci and changed the reject for incoming traffic to a drop, and disabled the ping rule. After that the GRC showed all ports as stealth and ping was unsuccessfull. So far everything good and as expected.
I think this is on turris OS v3. have to confirm.
Then i remember that on another flat i have also omnia installed (one of the units from early bidders indiegogo campaign) where i have not run the shields up. So i have run also GRC shields up from that router and it also showed that all ports are blocked only and ping allowed. So i made the same changes (to change it to drop and disable the ping rule), but the grc shields up are still showing port 1, TCP Mux as blocked only, not stealth. other ports are stealth and ping is unsuccessful.
I did not understand why it may show up, and i did not really had time to investigate, so i rather reflashed the router with latest medkit from hbs branch and configured it from scratch. Of course after completing the configuration guide the GRC shields up was showing as blocked only and ping allowed. so again i made changes to drop and disabled ping rule. but again the same problem the port 1 shows as blocked only instead of stealth. It seems strange to me.
Anybody care to elaborate what might be causing this ?
Both “sites” have same ISP and reserved static public IP via NAT 1:1 and the config is pretty bare bone, nothing fancy on those two sites.
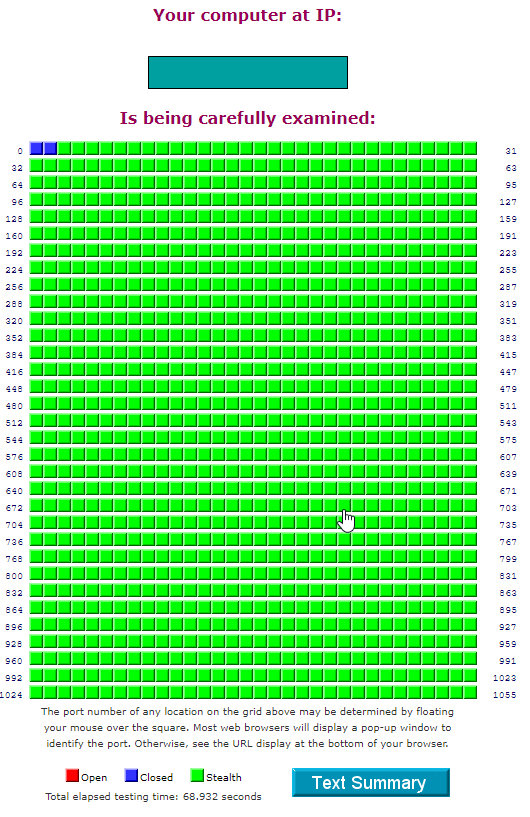
 ) etc.
) etc.