Hi there
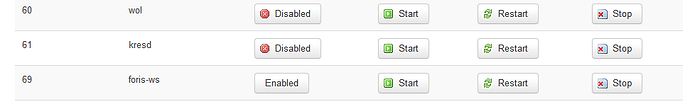
I’m running a TO with Turris OS version 3.11.23. In addition I did disable kresd for startup
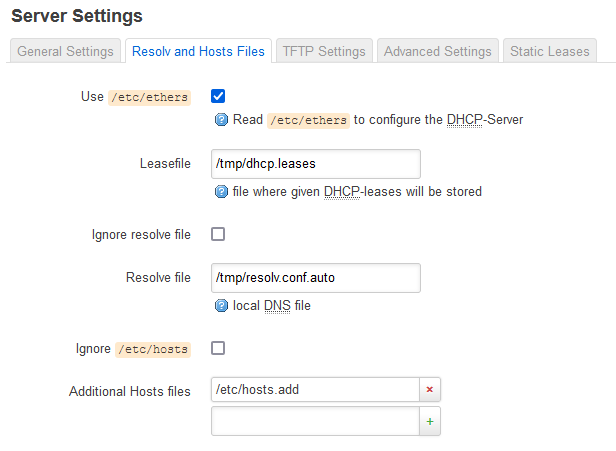
And run dsnmasq. The reason for dnsmasq is that I can add some custom domains for resolution in /etc/hosts.add
Now I setup a Raspberry Pi 4b that has installd AdGuard Home and it’s also setup to use the installed Unbound as recursive DNS server.
Basically I want domain resolution byDHCP going as follow:
(1) Check TO (especially the locally added domains in /etc/hosts.add
(2) If TO doesn’t know about the domain and has no valid cached information, go to the Raspberry Pi (AdGuard Home with a few blocking lists for ads).
(3) If AdGuard Home doesn’t have an answer, it will then use its local Unbound (127.0.0.1:5335) which will then do recursive lookup.
The problem is, that I can’t make the DHCP clients use the Raspberry Pi as DNS server.
Foris does not let me select add a custom DNS Server but only a few from a dropdown.
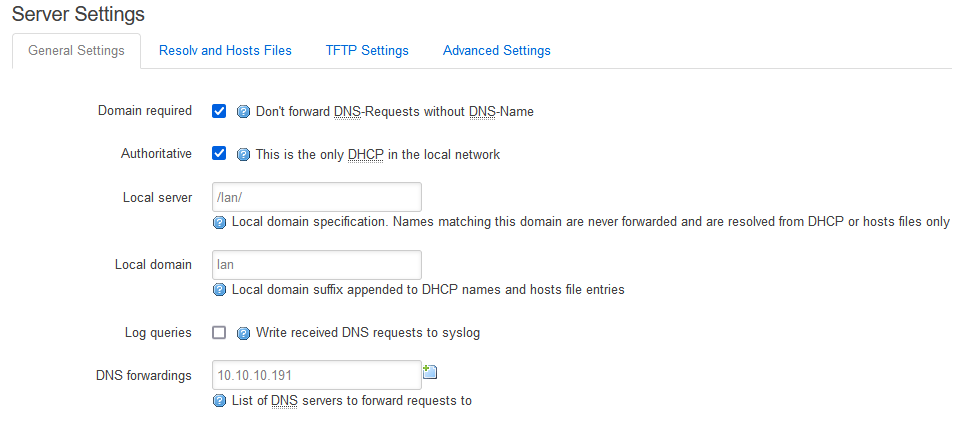
In LuCi I did go to the DHCP and DNS settings and added the Raspberrypi to the DNS forwardings screen. That did not help.
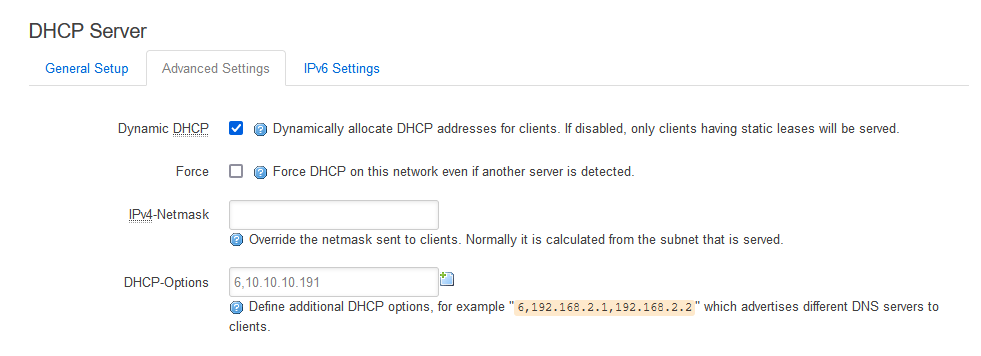
I then read that I need to go to Network → Interface → LAN → DHCP Server → Advanced Settings and set it there:
That did not help either.
In ever other no-name brand router I can setup easily what upstream DNS server to use. Why won’t it work in TO?
Also funny thing: Remember that I did disabled kresd from startup?
Well, sshing into the TO box and runnning ps | grep 53 returns this:
root@turris:~# ps | grep 53 2613 root 25396 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 2614 root 25396 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 2615 root 25396 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 2629 root 25396 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 2633 root 25396 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 2637 root 25300 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 2642 root 25396 S {foris-controlle} /usr/bin/python3.6 /usr/bin/foris-controller -b openwrt -C /var/run/foris-controller-client.sock ubus --path /var/run/ubus.sock 5135 root 42484 S /usr/bin/kresd -c /tmp/kresd.config -f 1 /tmp/kresd -a 0.0.0.0#53 -a ::#53 5331 root 0 SW [kworker/0:2] 5931 root 1108 S grep 53
How comes kresd is running when I did disable it?