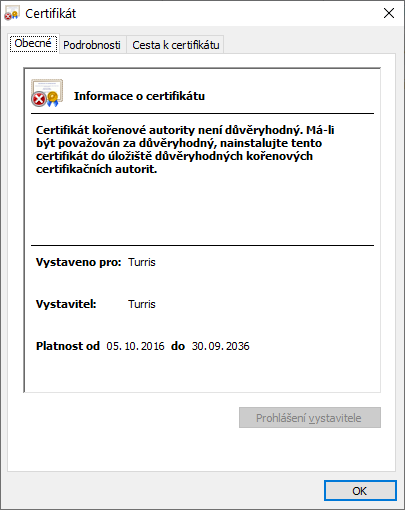
After the update from 3.11.xx to 5.3.2 I have the problem with the Turris certificate to set SSL for https://192.168.1.1/ as the system states “This CA root certificate is considered untrusted because it is not stored in the CA’s trusted root certificate store.” (Tento kořenový certifikát certifikační autority je považovaný za nedůvěryhodný, protože není uložen v úložišti důvěryhodných kořenových certifikátů certifikační autority.). Thank you for any advice on how to solve it.
i installed the cert+key bundle into /etc/lighttpd-self-signed.pem
and restarted lighthttpd.
Thank you, but I do not know where to get this bundle. I would like to use Turris certifikate, but I do not know where to get it:
I found, that there are significant differences in the ssl-enable.conf file.
In the previous OS 3.11.xx it looked like this (and it worked - it was created according to the instructions on https://blog.berkasimon.com/administrace-turrisu-s-vlastnim-ssl-certifikatem):
Preformatted text# This settings enables https with user-generated self-signed certificate from package https-cert
$SERVER[“socket”] == “:80” {
$HTTP[“host”] =~ “(.)" {
url.redirect = ( "^/(.)” => “https://%1/$1” )
}
}
$SERVER[“socket”] == “:443” {
ssl.engine = “enable”
ssl.use-sslv2 = “disable”
ssl.use-sslv3 = “disable”
ssl.pemfile = “/root/ssl/key-cert.pem”
ssl.ca-file = “/root/ssl/ca.cert”
}
$SERVER[“socket”] == “[::]:443” {
ssl.engine = “enable”
ssl.use-sslv2 = “disable”
ssl.use-sslv3 = “disable”
ssl.pemfile = “/root/ssl/key-cert.pem”
ssl.ca-file = “/root/ssl/ca.cert”
}
$HTTP[“scheme”] == “https” {
# Add ‘HTTP Strict Transport Security’ header (HSTS) to sites
# setenv.add-response-header += ( “Strict-Transport-Security” => “max-age=31536000; includeSubDomains” )
}
but in the OS 5.x the ssl-enable.conf is completely different:
Preformatted text# This settings enables https with user-generated self-signed certificate from
Preformatted text# package https-cert
Preformatted text# This package is not meant to be edited, it is part of package lighttpd-https-cert
Preformatted text# If you need different https setup, uninstall this package and create your own configuration
ssl.pemfile = “/etc/lighttpd-self-signed.pem”
ssl.openssl.ssl-conf-cmd = (
“MinProtocol” => “TLSv1.2”,
“Options” => “-ServerPreference”,
“CipherString” => “ECDHE+AESGCM:ECDHE+AES256:CHACHA20:!SHA1:!SHA256:!SHA384”
)
$SERVER[“socket”] == “:443” {
ssl.engine = “enable”
}
$SERVER[“socket”] == “[::]:443” {
ssl.engine = “enable”
}
and the “/etc/lighttpd-self-signed.pem” exists (it is default one after migration to OS 5.x). But problem remains.
Are there any similar instructions for the OS 5.x as they are for OS 3.x in https://blog.berkasimon.com/administrace-turrisu-s-vlastnim-ssl-certifikatem ?
I am sorry, I misunderstood what you wrote.
I have created my own key+certificate, created bundle by concatenating them and I simply replaced the /etc/lighttpd-self-signed.pem with my own certificate bundle.
what you see is that turris apparently created new certificate you don’t have trusted in your browser.
If you want to use “/root/ssl/key-cert.pem” and “/root/ssl/ca.cert” from your old system, and you still have them, you can concate them into /etc/lighttpd-self-signed.pem
echo | cat /root/ssl/key-cert.pem - /root/ssl/ca.cert > /etc/lighttpd-self-signed.pem
restart lighthttpd after.
Great, it works. Thank you very much.
This topic was automatically closed 3 days after the last reply. New replies are no longer allowed.