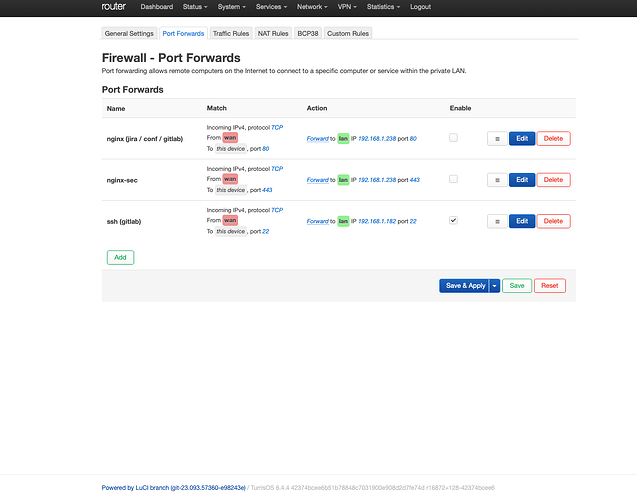
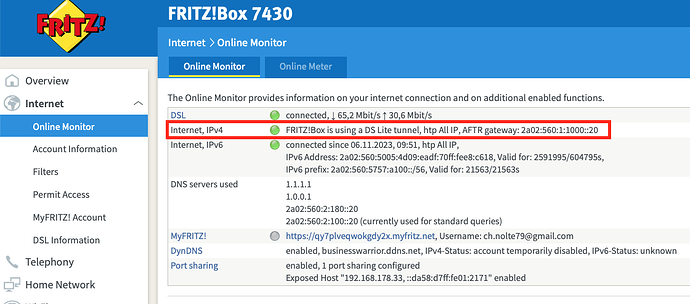
I am having trouble to get simple port forwarding rules to work.
The traffic is incoming on the turris:
root@router:~# tcpdump -i any port 22 and inbound and not src host 192.168.1.106
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
12:05:47.355189 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 353183265, win 2047, options [nop,nop,TS val 290517235 ecr 1205336816], length 0
12:05:47.355189 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 1, win 2047, options [nop,nop,TS val 290517235 ecr 1205337003,nop,nop,sack 1 {4294967261:1}], length 0
12:05:47.355553 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 37, win 2048, options [nop,nop,TS val 290517235 ecr 1205337006], length 0
12:05:47.355553 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [P.], seq 0:36, ack 37, win 2048, options [nop,nop,TS val 290517235 ecr 1205337006], length 36
12:05:47.355553 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [P.], seq 36:80, ack 37, win 2048, options [nop,nop,TS val 290517235 ecr 1205337006], length 44
12:05:47.498785 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 73, win 2047, options [nop,nop,TS val 290517378 ecr 1205337175], length 0
12:05:47.498905 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [P.], seq 80:116, ack 73, win 2048, options [nop,nop,TS val 290517378 ecr 1205337175], length 36
12:05:47.764113 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 109, win 2047, options [nop,nop,TS val 290517643 ecr 1205337276], length 0
12:05:47.764113 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 145, win 2048, options [nop,nop,TS val 290517643 ecr 1205337345], length 0
12:05:47.764489 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [P.], seq 116:152, ack 145, win 2048, options [nop,nop,TS val 290517643 ecr 1205337345], length 36
12:05:47.764490 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [P.], seq 152:204, ack 145, win 2048, options [nop,nop,TS val 290517643 ecr 1205337345], length 52
12:05:47.769163 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [P.], seq 204:380, ack 145, win 2048, options [nop,nop,TS val 290517649 ecr 1205337442], length 176
12:05:47.770846 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 181, win 2047, options [nop,nop,TS val 290517650 ecr 1205337447], length 0
12:05:47.770846 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 241, win 2048, options [nop,nop,TS val 290517650 ecr 1205337447], length 0
12:05:47.771674 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [.], ack 242, win 2048, options [nop,nop,TS val 290517650 ecr 1205337449], length 0
12:05:47.785427 IP 192.168.1.140.22 > 192.168.1.106.65085: Flags [F.], seq 380, ack 242, win 2048, options [nop,nop,TS val 290517665 ecr 1205337449], length 0
12:05:49.318724 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [S.], seq 583084176, ack 3354047146, win 28960, options [mss 1412,sackOK,TS val 1125267200 ecr 550632766,nop,wscale 11], length 0
12:05:49.318724 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [S.], seq 583084176, ack 3354047146, win 28960, options [mss 1412,sackOK,TS val 1125267200 ecr 550632766,nop,wscale 11], length 0
12:05:49.335404 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [.], ack 22, win 15, options [nop,nop,TS val 1125267217 ecr 550632783], length 0
12:05:49.335404 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [.], ack 22, win 15, options [nop,nop,TS val 1125267217 ecr 550632783], length 0
12:05:49.343628 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 1:22, ack 22, win 15, options [nop,nop,TS val 1125267225 ecr 550632783], length 21
12:05:49.343628 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 1:22, ack 22, win 15, options [nop,nop,TS val 1125267225 ecr 550632783], length 21
12:05:49.359232 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 22:1070, ack 22, win 15, options [nop,nop,TS val 1125267241 ecr 550632808], length 1048
12:05:49.359232 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 22:1070, ack 22, win 15, options [nop,nop,TS val 1125267241 ecr 550632808], length 1048
12:05:49.890463 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3450:3518, ack 3554, win 20, options [nop,nop,TS val 1125267772 ecr 550633328], length 68
12:05:49.890463 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3450:3518, ack 3554, win 20, options [nop,nop,TS val 1125267772 ecr 550633328], length 68
12:05:49.890463 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3518:3606, ack 3554, win 20, options [nop,nop,TS val 1125267772 ecr 550633328], length 88
12:05:49.890463 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3518:3606, ack 3554, win 20, options [nop,nop,TS val 1125267772 ecr 550633328], length 88
12:05:49.891604 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3606:3730, ack 3554, win 20, options [nop,nop,TS val 1125267773 ecr 550633328], length 124
12:05:49.891604 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3606:3730, ack 3554, win 20, options [nop,nop,TS val 1125267773 ecr 550633328], length 124
12:05:49.966244 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3606:3730, ack 3554, win 20, options [nop,nop,TS val 1125267848 ecr 550633343], length 124
12:05:49.966244 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3606:3730, ack 3554, win 20, options [nop,nop,TS val 1125267848 ecr 550633343], length 124
12:05:50.206905 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3450:3730, ack 3554, win 20, options [nop,nop,TS val 1125268088 ecr 550633343], length 280
12:05:50.206905 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [P.], seq 3450:3730, ack 3554, win 20, options [nop,nop,TS val 1125268088 ecr 550633343], length 280
12:05:50.436813 IP XXXXXXXXXX.nicesrv.de.22 > 192.168.178.33.65138: Flags [.], ack 3598, win 20, options [nop,nop,TS val 1125268319 ecr 550633839], length 0
But there is no outgoing traffic:
root@router:/etc/config# tcpdump -i br-lan port 22 and not src host 192.168.1.106 and not dst host 192.168.1.106
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on br-lan, link-type EN10MB (Ethernet), capture size 262144 bytes
^C
0 packets captured
1 packet received by filter
0 packets dropped by kernel
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option sentinel_fwlogs '1'
option sentinel_minipot '1'
option haas_proxy '1'
option sentinel_dynfw '1'
option input 'DROP'
option forward 'DROP'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone 'guest_turris'
option enabled '1'
list network 'guest_turris'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
option name 'tr_guest'
config forwarding 'guest_turris_forward_wan'
option enabled '1'
option name 'guest to wan forward'
option dest 'wan'
option src 'tr_guest'
config rule 'guest_turris_dns_rule'
option enabled '1'
option name 'guest dns rule'
option proto 'tcpudp'
option dest_port '53'
option target 'ACCEPT'
option src 'tr_guest'
config rule 'guest_turris_dhcp_rule'
option enabled '1'
option name 'guest dhcp rule'
option proto 'udp'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
option src 'tr_guest'
config rule 'wan_ssh_turris_rule'
option name 'wan_ssh_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '22'
option proto 'tcp'
option src 'wan'
config rule 'wan_http_turris_rule'
option name 'wan_http_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '80'
option proto 'tcp'
option src 'wan'
config rule 'wan_https_turris_rule'
option name 'wan_https_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '443'
option proto 'tcp'
option src 'wan'
config rule 'turris_wan_6in4_rule'
option enabled '0'
config zone 'turris_vpn_client'
option name 'tr_vpn_cl'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
config forwarding 'turris_vpn_client_forward'
option src 'lan'
option dest 'tr_vpn_cl'
config zone 'vpn_turris'
option enabled '1'
option name 'vpn_turris'
option input 'ACCEPT'
option forward 'REJECT'
option output 'ACCEPT'
option masq '1'
list network 'vpn_turris'
config rule 'vpn_turris_rule'
option enabled '1'
option name 'vpn_turris_rule'
option target 'ACCEPT'
option src 'wan'
option dest_port '1194'
option proto 'tcp'
config forwarding 'vpn_turris_forward_lan_in'
option enabled '1'
option src 'vpn_turris'
option dest 'lan'
config forwarding 'vpn_turris_forward_lan_out'
option enabled '1'
option src 'lan'
option dest 'vpn_turris'
config forwarding 'vpn_turris_forward_wan_out'
option enabled '0'
option src 'vpn_turris'
option dest 'wan'
config redirect
option src 'wan'
option name 'nginx (jira / conf / gitlab)'
option src_dport '80'
option target 'DNAT'
option dest_ip '192.168.1.238'
option dest 'lan'
list proto 'tcp'
option dest_port '80'
option enabled '0'
config redirect
option src 'wan'
option name 'nginx-sec'
option src_dport '443'
option target 'DNAT'
option dest_ip '192.168.1.238'
option dest 'lan'
list proto 'tcp'
option dest_port '443'
option enabled '0'
config redirect
option src 'wan'
option name 'ssh (gitlab)'
option src_dport '22'
option target 'DNAT'
option dest_ip '192.168.1.182'
list proto 'tcp'
option dest_port '22'
option dest 'lan'
option enabled '1'
config include 'bcp38'
option type 'script'
option path '/usr/lib/bcp38/run.sh'
option family 'IPv4'
option reload '1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config rule
option src 'wan'
option target 'DROP'
option proto 'all'
option extra '-m limit --limit 3/min --limit-burst 10 -j LOG --log-prefix "FW_DROP: "'
The target system 192.168.1.182 is pingable as well as ssh is working from the turris to the .182 box.
I cannot seem to find the issue and I think that I have hit a bug somehow.