I recently had to reinstall from MedKit because my internal drive was full (despite having moved lxc to a usb flash drive, pakon, which I didn’t install, and schnapps were eating away at my storage). I am trying to install OpenVPN again since it stopped working. I was having trouble so I upgraded to 3.11.3RC and regenerated my CA and client certs & conf files from scratch. They don’t appear to be using compression anymore which was one of the issues reported here:
Still no Dice.
I’m actually able to connect, but no traffic is making it to the server. Here are the pertinent conf files:
/etc/config/openvpn
config openvpn 'server_turris'
option enabled '1'
option port '1194'
option dev 'tun_turris'
option ca '/etc/ssl/ca/openvpn/ca.crt'
option crl_verify '/etc/ssl/ca/openvpn/ca.crl'
option cert '/etc/ssl/ca/openvpn/01.crt'
option key '/etc/ssl/ca/openvpn/01.key'
option dh '/etc/dhparam/dh-default.pem'
option server '10.111.111.0 255.255.255.0'
option ifconfig_pool_persist '/tmp/ipp.txt'
option duplicate_cn '0'
option keepalive '10 120'
option persist_key '1'
option persist_tun '1'
option status '/tmp/openvpn-status.log'
option verb '3'
option mute '20'
option proto 'udp' # have also tried: option proto 'tcp-server'
list push 'route 192.168.11.0 255.255.255.0'
turris.conf
##############################################
# Openvpn client configuration generated by #
# router Turris based on Sample client-side #
# OpenVPN 2.0 config file #
# #
# This configuration can be used only on #
# a single client. #
# #
# #
# On Windows, you might want to rename this #
# file so it has a .ovpn extension #
##############################################
client
# Use the same setting as you are using on
# the server.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
dev tun_turris
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel
# if you have more than one. On XP SP2,
# you may need to disable the firewall
# for the TAP adapter.
;dev-node MyTap
proto udp # have also tried: proto tcp-server
# The hostname/IP and port of the server.
# You can have multiple remote entries
# to load balance between the servers.
;remote my-server-1 1194
;remote my-server-2 1194
remote IP_ADDRESS_HIDDEN 1194
# Choose a random host from the remote
# list for load-balancing. Otherwise
# try hosts in the order specified.
;remote-random
# Keep trying indefinitely to resolve the
# host name of the OpenVPN server. Very useful
# on machines which are not permanently connected
# to the internet such as laptops.
resolv-retry infinite
# Most clients don't need to bind to
# a specific local port number.
nobind
# Downgrade privileges after initialization (non-Windows only)
;user nobody
;group nobody
# Try to preserve some state across restarts.
persist-key
persist-tun
# If you are connecting through an
# HTTP proxy to reach the actual OpenVPN
# server, put the proxy server/IP and
# port number here. See the man page
# if your proxy server requires
# authentication.
;http-proxy-retry # retry on connection failures
;http-proxy [proxy server] [proxy port #]
# Wireless networks often produce a lot
# of duplicate packets. Set this flag
# to silence duplicate packet warnings.
mute-replay-warnings
<ca>
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
</ca>
<cert>...</cert>
<key>...</key>
remote-cert-tls server
# Set log file verbosity.
verb 3
# Silence repeating messages
;mute 20
# To enable to process DNS push request from the server on linux machines (non systemd-resolved)
# note that you might need to have resolvconf program installed
;script-security 2
;up /etc/openvpn/update-resolv-conf
;down /etc/openvpn/update-resolv-conf
# To enable to process DNS push request from the server on linux machines (systemd-resolved)
# see https://github.com/jonathanio/update-systemd-resolved
;script-security 2
;setenv PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
;up /etc/openvpn/update-systemd-resolved
;down /etc/openvpn/update-systemd-resolved
;down-pre
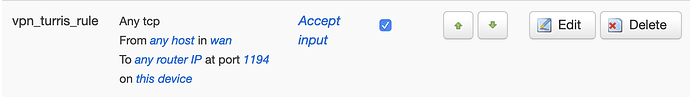
I have not modified the Firewall Traffic Rules, and it does contain:
I can still browse the web when connected, unless I activate:
All traffic through vpn, orUse DNS from vpn
I can see the additional network routes added when I look with
netstat -nr -f inet
Destination Gateway Flags Refs Use Netif Expire
10.111.111.1/32 10.111.111.5 UGSc 0 0 utun2
10.111.111.5 10.111.111.6 UH 12 0 utun2
192.168.11 10.111.111.5 UGSc 10 0 utun2
But when I try to ping the remote network:
$ ping 10.111.111.5
PING 10.111.111.5 (10.111.111.5): 56 data bytes
Request timeout for icmp_seq 0
$ ping 192.168.11.1
PING 192.168.11.1 (192.168.11.1): 56 data bytes
Request timeout for icmp_seq 0
I have tried connecting to the server from Android, iOS, MacOS (with Tunnelblick & OpenVPN) same result on all platforms.
If you want me to share any traceroutes our tcpdumps, or Tunnelblick logs, just let me know. Any help appreciated.
Thanks,
Daniel