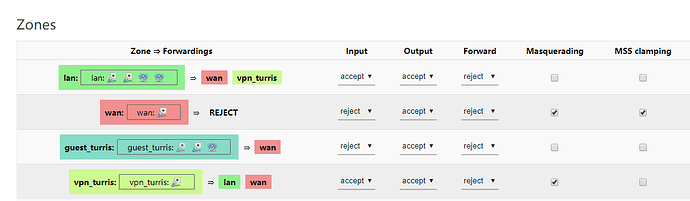
there are more names but for example
vpn_turris_rule Any udp
From any host in wan
To any router IP at port 1194 on this device Accept input
this is naturally enabled like the rest of rules.
there are no ports open, no forward rules and no source nat values
ok. i tested the official version of openvpn. used mobile data (real case scenario)
log
19:34:44.283 – ----- OpenVPN Start -----
19:34:44.285 – EVENT: CORE_THREAD_ACTIVE
19:34:44.289 – OpenVPN core 3.git::728733ae:Release android arm64 64-bit PT_PROXY built on Aug 14 2019 14:13:26
19:34:44.314 – Frame=512/2048/512 mssfix-ctrl=1250
19:34:44.324 – UNUSED OPTIONS
4 [resolv-retry] [infinite]
5 [nobind]
6 [persist-key]
7 [persist-tun]
8 [mute-replay-warnings]
13 [verb] [3]
19:34:44.332 – EVENT: RESOLVE
19:34:44.352 – Contacting xxx:1194 via UDP
19:34:44.354 – EVENT: WAIT
19:34:44.387 – Connecting to [xxx]:1194 (xxx) via UDPv4
19:34:44.423 – EVENT: CONNECTING
19:34:44.433 – Tunnel Options:V4,dev-type tun,link-mtu 1541,tun-mtu 1500,proto UDPv4,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client
19:34:44.434 – Creds: UsernameEmpty/PasswordEmpty
19:34:44.437 – Peer Info:
IV_GUI_VER=OC30Android
IV_VER=3.git::728733ae:Release
IV_PLAT=android
IV_NCP=2
IV_TCPNL=1
IV_PROTO=2
IV_AUTO_SESS=1
IV_BS64DL=1
19:34:44.738 – VERIFY OK : depth=1
cert. version : 3
serial number : xxx
issuer name : CN=openvpn
subject name : CN=openvpn
issued on : 2019-09-02 19:01:30
expires on : 2029-08-30 19:01:30
signed using : RSA with SHA-256
RSA key size : 4096 bits
basic constraints : CA=true
subject alt name :
cert. type : SSL CA
key usage : Key Cert Sign, CRL Sign
19:34:44.740 – VERIFY OK : depth=0
cert. version : 3
serial number : 01
issuer name : CN=openvpn
subject name : CN=turris
issued on : 2019-09-02 19:02:06
expires on : 2029-08-30 19:02:06
signed using : RSA with SHA-256
RSA key size : 4096 bits
basic constraints : CA=false
cert. type : SSL Server
key usage : Digital Signature, Key Encipherment
ext key usage : TLS Web Server Authentication
19:34:45.173 – SSL Handshake: TLSv1.2/TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384
19:34:45.175 – Session is ACTIVE
19:34:45.176 – EVENT: GET_CONFIG
19:34:45.189 – Sending PUSH_REQUEST to server…
19:34:45.222 – OPTIONS:
0 [route] [192.168.1.0] [255.255.255.0]
1 [redirect-gateway] [def1]
2 [dhcp-option] [DNS] [10.111.111.1]
3 [route] [10.111.111.1]
4 [topology] [net30]
5 [ping] [10]
6 [ping-restart] [120]
7 [ifconfig] [10.111.111.6] [10.111.111.5]
8 [peer-id] [0]
9 [cipher] [AES-256-GCM]
19:34:45.224 – PROTOCOL OPTIONS:
cipher: AES-256-GCM
digest: SHA1
compress: NONE
peer ID: 0
19:34:45.225 – EVENT: ASSIGN_IP
19:34:45.255 – Connected via tun
19:34:45.257 – EVENT: CONNECTED info=‘xxx:1194 (xxx) via /UDPv4 on tun/10.111.111.6/ gw=[10.111.111.5/]’ trans=TO_CONNECTED
19:36:54.633 – EVENT: CORE_THREAD_INACTIVE trans=TO_DISCONNECTED
19:36:54.635 – Tunnel bytes per CPU second: 0
19:36:54.637 – ----- OpenVPN Stop -----
same problem, connects fine but no data transmitted - cant find any webpages etc.