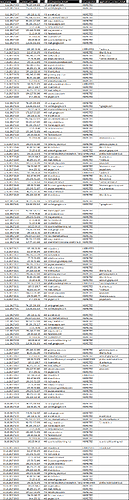
My Omnia WAN side is protected by another firewall (Untangle) to see and verify what is possibly leaking out from Omnia to WAN (Untangle WAN public IP1 - Omnia WAN public IP2 but in DMZ of Untangle).
I noticed periodical batches of HTTPS connections (and few SMTP) usualy once per day on sites I do not use. What is strange that most of them are .cz and related to banking. After few days investigating I could not find any device or source for those connections. Finaly I left my Omnia with no clients (even LXCs) connected. But still the same connections were leaking from Omnia to internet (table below truncated for last few days).
I’m sure there’s nothing additionaly installed to generate traffic like this except for Omnia defaults. I belive some system defaults are generating this traffic. Maybe CZ.NIC intention to check some TLS on popular services?
Anyway I don’t like that my super-router does something I don’t know about and what cannot be controlled.
Any hints from you guys or CZ.NIC?
Thank you…
time_stamp s_server_addr s_server_port ssl_inspector_detail ssl_inspector_status application_control_detail
8.11.2017 9:03 74.125.206.108 25 smtp.gmail.com INSPECTED
8.11.2017 9:03 216.58.201.110 443 wallet.google.com INSPECTED
8.11.2017 3:47 160.218.11.32 443 e-ucet.o2.cz INSPECTED
8.11.2017 3:47 195.234.207.123 443 ibs.internetbanka.cz INSPECTED
8.11.2017 3:47 93.153.117.139 443 muj.t-mobile.cz INSPECTED
8.11.2017 3:47 95.100.178.217 443 itunes.apple.com INSPECTED
8.11.2017 3:47 77.75.78.48 25 smtp.seznam.cz INSPECTED
8.11.2017 3:47 193.245.72.151 443 muj.erasvet.cz INSPECTED
8.11.2017 3:47 31.13.84.36 443 facebook.com INSPECTED
8.11.2017 3:47 91.139.8.86 443 ib.creditas.cz INSPECTED
8.11.2017 3:45 162.25.64.10 443 cz.unicreditbanking.net INSPECTED
8.11.2017 3:45 216.58.201.101 443 mail.google.com INSPECTED
7.11.2017 21:56 185.189.33.61 443 ssl.aukro.cz UNTRUSTED *.aukro.cz
7.11.2017 21:56 212.67.66.170 443 klient3.rb.cz INSPECTED klient3.rb.cz
7.11.2017 21:56 193.245.72.229 443 ib24.csob.cz INSPECTED ib24.csob.cz
7.11.2017 21:56 77.75.76.150 443 email.seznam.cz INSPECTED *.email.seznam.cz
7.11.2017 21:56 193.58.72.141 443 3dsecure.gpwebpay.com INSPECTED
7.11.2017 21:56 193.245.72.157 443 paysec.erasvet.cz INSPECTED
7.11.2017 21:56 46.255.231.36 443 mail.centrum.cz INSPECTED
7.11.2017 21:56 194.228.112.60 443 klient2.rb.cz INSPECTED
7.11.2017 21:56 193.245.32.180 443 gateway.paysec.cz INSPECTED
7.11.2017 21:56 82.99.162.240 443 klient1.rb.cz INSPECTED
7.11.2017 21:56 35.159.8.35 443 account.gopay.com INSPECTED
7.11.2017 21:56 193.58.72.171 443 platba.mobitoplatito.cz UNTRUSTED
7.11.2017 21:56 185.33.156.7 443 ib.airbank.cz INSPECTED
7.11.2017 21:56 46.255.231.37 443 mail.volny.cz INSPECTED
7.11.2017 21:56 104.127.59.249 443 secure.payu.com INSPECTED
7.11.2017 21:55 64.4.250.32 443 paypal.com INSPECTED
6.11.2017 8:26 74.125.206.108 25 smtp.gmail.com INSPECTED
6.11.2017 8:26 216.58.201.110 443 wallet.google.com INSPECTED *.google.com
6.11.2017 3:30 162.25.64.10 443 cz.unicreditbanking.net INSPECTED
6.11.2017 3:30 172.217.23.229 443 mail.google.com INSPECTED
6.11.2017 3:25 160.218.11.32 443 e-ucet.o2.cz INSPECTED
6.11.2017 3:25 195.234.207.123 443 ibs.internetbanka.cz INSPECTED
6.11.2017 3:25 93.153.117.139 443 muj.t-mobile.cz INSPECTED
6.11.2017 3:25 95.100.178.217 443 itunes.apple.com INSPECTED
6.11.2017 3:25 77.75.78.48 25 smtp.seznam.cz INSPECTED
6.11.2017 3:25 193.245.72.151 443 muj.erasvet.cz INSPECTED
6.11.2017 3:25 185.60.216.35 443 facebook.com INSPECTED
6.11.2017 3:25 91.139.8.86 443 ib.creditas.cz INSPECTED www.creditas.cz
5.11.2017 21:45 193.245.32.180 443 gateway.paysec.cz INSPECTED gateway.paysec.cz
5.11.2017 21:45 82.99.162.240 443 klient1.rb.cz INSPECTED klient1.rb.cz
5.11.2017 21:45 35.159.8.35 443 account.gopay.com INSPECTED account.gopay.com
5.11.2017 21:45 193.58.72.171 443 Server SSL decrypt exception: handshake alert: unrecognized_name ABANDONED platba.mobitoplatito.cz
5.11.2017 21:45 185.33.156.7 443 ib.airbank.cz INSPECTED ib.airbank.cz
5.11.2017 21:45 46.255.231.37 443 mail.volny.cz INSPECTED *.volny.cz
5.11.2017 21:45 104.127.59.249 443 secure.payu.com INSPECTED payu.com
5.11.2017 21:45 194.50.240.77 443 3dsecure.csas.cz INSPECTED 3dsecure.csas.cz
5.11.2017 21:45 64.4.250.32 443 paypal.com INSPECTED paypal.com
5.11.2017 21:45 185.189.33.61 443 ssl.aukro.cz UNTRUSTED *.aukro.cz
5.11.2017 21:45 212.67.66.170 443 klient3.rb.cz INSPECTED klient3.rb.cz
5.11.2017 21:45 193.245.72.229 443 ib24.csob.cz INSPECTED ib24.csob.cz
5.11.2017 21:45 77.75.78.150 443 email.seznam.cz INSPECTED *.email.seznam.cz
5.11.2017 21:45 193.58.72.141 443 3dsecure.gpwebpay.com INSPECTED 3dsecure.gpwebpay.com
5.11.2017 21:45 193.245.72.157 443 paysec.erasvet.cz INSPECTED muj.erasvet.cz
5.11.2017 21:45 46.255.231.36 443 mail.centrum.cz INSPECTED
5.11.2017 21:45 194.228.112.60 443 klient2.rb.cz INSPECTED klient2.rb.cz
4.11.2017 6:41 74.125.206.108 25 smtp.gmail.com INSPECTED
4.11.2017 6:41 216.58.201.110 443 wallet.google.com INSPECTED *.google.com
4.11.2017 2:20 95.100.178.217 443 itunes.apple.com INSPECTED
4.11.2017 2:20 77.75.76.48 25 smtp.seznam.cz INSPECTED
4.11.2017 2:20 193.245.72.151 443 muj.erasvet.cz INSPECTED
4.11.2017 2:20 31.13.84.36 443 facebook.com INSPECTED
4.11.2017 2:20 91.139.8.86 443 ib.creditas.cz INSPECTED
4.11.2017 2:18 162.25.64.10 443 cz.unicreditbanking.net INSPECTED
4.11.2017 2:18 216.58.201.101 443 mail.google.com INSPECTED
4.11.2017 2:14 160.218.11.32 443 e-ucet.o2.cz INSPECTED
4.11.2017 2:14 195.234.207.123 443 ibs.internetbanka.cz INSPECTED
4.11.2017 2:14 93.153.117.139 443 muj.t-mobile.cz INSPECTED
4.11.2017 2:14 217.77.163.160 443 onenetsamoobsluha.vodafone.cz INSPECTED
3.11.2017 21:21 185.189.33.61 443 ssl.aukro.cz UNTRUSTED
3.11.2017 21:21 212.67.66.170 443 klient3.rb.cz INSPECTED
3.11.2017 21:21 193.245.72.229 443 ib24.csob.cz INSPECTED
3.11.2017 21:21 77.75.78.150 443 email.seznam.cz INSPECTED
3.11.2017 21:21 193.58.72.141 443 3dsecure.gpwebpay.com INSPECTED
3.11.2017 21:21 193.245.72.157 443 paysec.erasvet.cz INSPECTED
3.11.2017 21:21 46.255.231.36 443 mail.centrum.cz INSPECTED
3.11.2017 21:21 194.228.112.60 443 klient2.rb.cz INSPECTED klient2.rb.cz
3.11.2017 21:21 193.245.32.180 443 gateway.paysec.cz INSPECTED gateway.paysec.cz
3.11.2017 21:21 82.99.162.240 443 klient1.rb.cz INSPECTED klient1.rb.cz
3.11.2017 21:21 35.159.8.35 443 account.gopay.com INSPECTED account.gopay.com
3.11.2017 21:21 193.58.72.171 443 platba.mobitoplatito.cz UNTRUSTED *.mobitoplatito.cz
3.11.2017 21:21 185.33.156.7 443 ib.airbank.cz INSPECTED ib.airbank.cz
3.11.2017 21:21 46.255.231.37 443 mail.volny.cz INSPECTED *.volny.cz
3.11.2017 21:21 104.127.59.249 443 secure.payu.com INSPECTED payu.com
3.11.2017 21:21 194.50.240.77 443 3dsecure.csas.cz INSPECTED 3dsecure.csas.cz
3.11.2017 21:21 64.4.250.32 443 paypal.com INSPECTED paypal.com
2.11.2017 7:21 74.125.206.108 25 smtp.gmail.com INSPECTED
2.11.2017 7:21 216.58.201.110 443 wallet.google.com INSPECTED
2.11.2017 1:00 160.218.11.32 443 e-ucet.o2.cz INSPECTED
2.11.2017 1:00 195.234.205.123 443 ibs.internetbanka.cz INSPECTED
2.11.2017 1:00 93.153.117.139 443 muj.t-mobile.cz INSPECTED
2.11.2017 1:00 95.100.178.217 443 itunes.apple.com INSPECTED
2.11.2017 1:00 77.75.78.48 25 smtp.seznam.cz INSPECTED
2.11.2017 1:00 193.245.72.151 443 muj.erasvet.cz INSPECTED
2.11.2017 1:00 185.60.216.35 443 facebook.com INSPECTED
2.11.2017 1:00 91.139.8.86 443 ib.creditas.cz INSPECTED
2.11.2017 0:58 162.25.64.10 443 cz.unicreditbanking.net INSPECTED
2.11.2017 0:58 216.58.201.101 443 mail.google.com INSPECTED
1.11.2017 21:07 193.245.32.180 443 gateway.paysec.cz INSPECTED gateway.paysec.cz
1.11.2017 21:07 82.99.162.240 443 klient1.rb.cz INSPECTED klient1.rb.cz
1.11.2017 21:07 35.159.8.35 443 account.gopay.com INSPECTED account.gopay.com
1.11.2017 21:07 193.58.72.171 443 Server SSL decrypt exception: handshake alert: unrecognized_name ABANDONED platba.mobitoplatito.cz
1.11.2017 21:07 185.33.156.7 443 ib.airbank.cz INSPECTED ib.airbank.cz
1.11.2017 21:07 46.255.231.37 443 mail.volny.cz INSPECTED *.volny.cz
1.11.2017 21:07 104.127.59.249 443 secure.payu.com INSPECTED payu.com
1.11.2017 21:07 64.4.250.32 443 paypal.com INSPECTED
1.11.2017 21:07 185.189.33.61 443 ssl.aukro.cz UNTRUSTED
1.11.2017 21:07 212.67.66.170 443 klient3.rb.cz INSPECTED
1.11.2017 21:07 193.245.72.229 443 ib24.csob.cz INSPECTED
1.11.2017 21:07 77.75.76.150 443 email.seznam.cz INSPECTED
1.11.2017 21:06 193.58.72.141 443 3dsecure.gpwebpay.com INSPECTED
1.11.2017 21:06 193.245.72.157 443 paysec.erasvet.cz INSPECTED
1.11.2017 21:06 46.255.231.36 443 mail.centrum.cz INSPECTED
1.11.2017 21:06 194.228.112.60 443 klient2.rb.cz INSPECTED
31.10.2017 5:28 74.125.206.108 25 smtp.gmail.com INSPECTED
31.10.2017 5:28 216.58.201.78 443 wallet.google.com INSPECTED
31.10.2017 1:35 216.58.214.197 443 mail.google.com INSPECTED
31.10.2017 1:30 160.218.11.32 443 e-ucet.o2.cz INSPECTED e-ucet.o2.cz
31.10.2017 1:30 195.234.205.123 443 ibs.internetbanka.cz INSPECTED ibs.internetbanka.cz
31.10.2017 1:30 93.153.117.139 443 muj.t-mobile.cz INSPECTED *.t-mobile.cz
31.10.2017 1:30 95.100.178.217 443 itunes.apple.com INSPECTED
31.10.2017 1:30 77.75.78.48 25 smtp.seznam.cz INSPECTED
31.10.2017 1:30 193.245.72.151 443 muj.erasvet.cz INSPECTED
31.10.2017 1:30 185.60.216.35 443 facebook.com INSPECTED
31.10.2017 1:30 91.139.8.86 443 ib.creditas.cz INSPECTED
31.10.2017 1:28 162.25.64.10 443 cz.unicreditbanking.net INSPECTED cz.unicreditbanking.net
30.10.2017 20:00 185.189.33.61 443 ssl.aukro.cz UNTRUSTED ssl.aukro.cz
30.10.2017 20:00 212.67.66.170 443 klient3.rb.cz INSPECTED
30.10.2017 20:00 193.245.72.229 443 ib24.csob.cz INSPECTED
30.10.2017 20:00 77.75.78.150 443 email.seznam.cz INSPECTED
30.10.2017 20:00 193.58.72.141 443 3dsecure.gpwebpay.com INSPECTED
30.10.2017 20:00 193.245.72.157 443 paysec.erasvet.cz INSPECTED
30.10.2017 20:00 46.255.231.36 443 mail.centrum.cz INSPECTED
30.10.2017 20:00 194.228.112.60 443 klient2.rb.cz INSPECTED
30.10.2017 20:00 193.245.32.180 443 gateway.paysec.cz INSPECTED
30.10.2017 20:00 82.99.162.240 443 klient1.rb.cz INSPECTED
30.10.2017 20:00 35.159.8.35 443 account.gopay.com INSPECTED
30.10.2017 20:00 193.58.72.171 443 Server SSL decrypt exception: handshake alert: unrecognized_name ABANDONED platba.mobitoplatito.cz
30.10.2017 20:00 185.33.156.7 443 ib.airbank.cz INSPECTED
30.10.2017 20:00 46.255.231.37 443 mail.volny.cz INSPECTED
30.10.2017 20:00 104.127.59.249 443 secure.payu.com INSPECTED
30.10.2017 20:00 194.50.240.77 443 3dsecure.csas.cz INSPECTED
30.10.2017 20:00 64.4.250.32 443 paypal.com INSPECTED