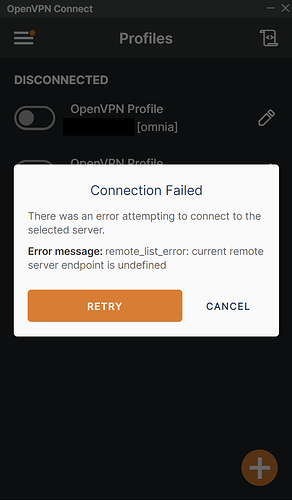
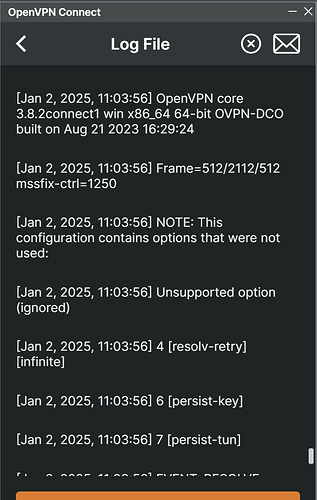
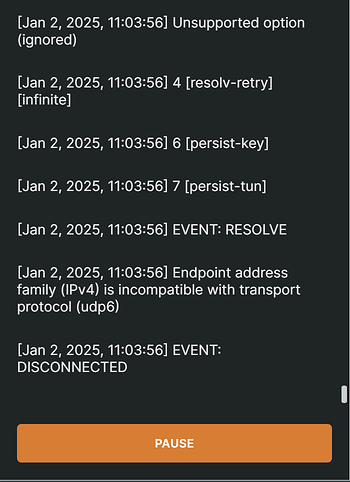
Hi all, my OpenVPN config does not work, please could anyone advise why?
CLIENT
openvpn version, running on SailfishOS:
OpenVPN 2.6.9 aarch64-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
library versions: OpenSSL 1.1.1v FIPS 1 Aug 2023, LZO 2.10
Originally developed by James Yonan
Copyright (C) 2002-2023 OpenVPN Inc <sales@openvpn.net>
Compile time defines: enable_async_push=no enable_comp_stub=no enable_crypto_ofb_cfb=yes enable_dco=no enable_dco_arg=auto enable_debug=yes enable_dependency_tracking=no enable_dlopen=unknown enable_dlopen_self=unknown enable_dlopen_self_static=unknown enable_fast_install=yes enable_fragment=yes enable_iproute2=yes enable_libtool_lock=yes enable_lz4=yes enable_lzo=yes enable_management=yes enable_pam_dlopen=no enable_password_save=yes enable_pedantic=no enable_pkcs11=no enable_plugin_auth_pam=yes enable_plugin_down_root=yes enable_plugins=yes enable_port_share=yes enable_selinux=no enable_shared=yes enable_shared_with_static_runtimes=no enable_small=no enable_static=no enable_strict=no enable_strict_options=no enable_systemd=yes enable_werror=no enable_win32_dll=yes enable_wolfssl_options_h=yes enable_x509_alt_username=yes with_aix_soname=aix with_crypto_library=openssl with_gnu_ld=yes with_mem_check=no with_openssl_engine=auto with_sysroot=no
client log repeats this message:
Jan 01 17:50:44 openvpn[26580]: Note: --cipher is not set. OpenVPN versions before 2.5 defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
Jan 01 17:50:44 openvpn[26580]: Options error: If you use one of --cert or --key, you must use them both
Jan 01 17:50:44 openvpn[26580]: Use --help for more information.
Jan 01 17:50:46 openvpn[26630]: Note: --cipher is not set. OpenVPN versions before 2.5 defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
Jan 01 17:50:46 openvpn[26630]: Options error: If you use one of --cert or --key, you must use them both
Jan 01 17:50:46 openvpn[26630]: Use --help for more information.
OMNIA
fresh install from factory image
TurrisOS 7.1.2, Turris Omnia
I followed these settings: OpenVPN server - Turris Documentation
VPN network is set to 10.0.1.0 / 255.255.255.0:
server log repeats this message:
Jan 1 16:53:46 openvpn(server_turris)[5869]: Initialization Sequence Completed
Jan 1 16:53:52 openvpn(server_turris)[5869]: event_wait : Interrupted system call (code=4)
Jan 1 16:53:52 openvpn(server_turris)[5869]: /usr/libexec/openvpn-hotplug route-pre-down server_turris tun_turris 1500 1621 10.0.1.1 255.255.255.0 init
Jan 1 16:53:52 openvpn(server_turris)[5869]: WARNING: Failed running command (--up/--down): external program exited with error status: 2
Jan 1 16:53:52 openvpn(server_turris)[5869]: Exiting due to fatal error
Jan 1 16:53:52 openvpn(server_turris)[7008]: --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
Jan 1 16:53:52 openvpn(server_turris)[7008]: OpenVPN 2.5.8 arm-openwrt-linux-muslgnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Jan 1 16:53:52 openvpn(server_turris)[7008]: library versions: OpenSSL 1.1.1w 11 Sep 2023, LZO 2.10
Jan 1 16:53:52 openvpn(server_turris)[7008]: net_route_v4_best_gw query: dst 0.0.0.0
Jan 1 16:53:52 openvpn(server_turris)[7008]: net_route_v4_best_gw result: via 10.10.10.1 dev pppoe-wan
Jan 1 16:53:52 openvpn(server_turris)[7008]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 1 16:53:52 openvpn(server_turris)[7008]: Diffie-Hellman initialized with 4096 bit key
Jan 1 16:53:52 openvpn(server_turris)[7008]: CRL: loaded 1 CRLs from file /etc/ssl/ca/openvpn/ca.crl
Jan 1 16:53:52 openvpn(server_turris)[7008]: TUN/TAP device tun_turris opened
Jan 1 16:53:52 openvpn(server_turris)[7008]: net_iface_mtu_set: mtu 1500 for tun_turris
Jan 1 16:53:52 openvpn(server_turris)[7008]: net_iface_up: set tun_turris up
Jan 1 16:53:52 openvpn(server_turris)[7008]: net_addr_v4_add: 10.0.1.1/24 dev tun_turris
Jan 1 16:53:52 openvpn(server_turris)[7008]: /usr/libexec/openvpn-hotplug up server_turris tun_turris 1500 1621 10.0.1.1 255.255.255.0 init
Jan 1 16:53:56 openvpn(server_turris)[7008]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Jan 1 16:53:56 openvpn(server_turris)[7008]: setsockopt(IPV6_V6ONLY=0)
Jan 1 16:53:56 openvpn(server_turris)[7008]: UDPv6 link local (bound): [AF_INET6][undef]:1194
Jan 1 16:53:56 openvpn(server_turris)[7008]: UDPv6 link remote: [AF_UNSPEC]
Jan 1 16:53:56 openvpn(server_turris)[7008]: MULTI: multi_init called, r=256 v=256
Jan 1 16:53:56 openvpn(server_turris)[7008]: IFCONFIG POOL IPv4: base=10.0.1.2 size=253
Jan 1 16:53:56 openvpn(server_turris)[7008]: IFCONFIG POOL LIST
Jan 1 16:53:56 openvpn(server_turris)[7008]: Initialization Sequence Completed