“how do i add a line of text to a textfile” never gets old 
We were all n00bs once. Some of us quite a long time ago - like 38 years 
hostapd (which is used by turris OS) already supports WPA3, so the main thing needed is for devs to update package to latest git
https://www.spinics.net/lists/hostap/msg04294.html
Edit:
and by hostapd I mean binary:
# ps aux|grep hostapd
root 4463 0.1 0.0 2100 1256 ? Ss Jun28 103:30 /usr/sbin/hostapd -P /var/run/wifi-phy1.pid -B /var/run/hostapd-phy1.conf
root 4494 0.0 0.0 2100 720 ? Ss Jun28 10:13 /usr/sbin/hostapd -P /var/run/wifi-phy0.pid -B /var/run/hostapd-phy0.conf
hostapd does not appear being installed by default but hostapd-common (2016-12-19-7).
Synology routers support WPA3-Personal and Enterprise.
LANCOM with their latest firmware update started support
According to https://openwrt.org/docs/guide-user/network/wifi/basic OpenWRT 19.01 will feature support for WPA3
Hostapd released v2.7, it has SEA support.
http://w1.fi/cgit/hostap/plain/hostapd/ChangeLog
Not sure if Hostapd can be upgraded or if we need to wait for Turris 4.0
development chain is master source (w1.fi) → OpenWRT → TO
OWRT is currently patching for their upcoming 19.x release and thus far not backporting to their 18.x/15.x branches, latter being the source for the current TOS 3.x branch.
We update hostapd and wpad to apply security patches but don’t expect new versions of packages to be backported. Someone might get around to it but most probably this issue is going to be closed together with 3.x release cycle some time in future.
seems that WPA3 is plagued by a number of underlying design flaws which expose users to password partitioning attacks…
https://www.wi-fi.org/news-events/newsroom/wi-fi-alliance-security-update-april-2019
He has a website explaining all this
https://wpa3.mathyvanhoef.com
requires wpad-openssl or wpad-wolfssl which currently not installed by default.
WPA3 plagued by new vulnerabilities that being introduced with the patches trying to fix earlier attack vectors…
Might be even safer to stay with WPA2 instead
Here we go ![]()
Patch on patch and countermeasure on countermeasure…
There are voices/opinions reckoning that WPA3 is broken by design (ill conceived) and cannot be fixed/patched and instead a new standard 3.x(1?) to be developed which likely will be incompatible with 3.0
The researchers even discovered one CPE vendor implementing WPA3 in a weakened state, performing less cryptographic operations than specified in the WPA3 standard, potentially because their hardware not being able to do so…
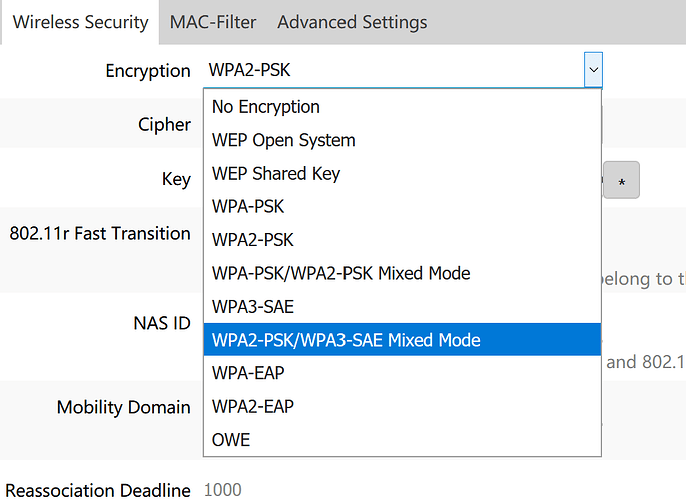
Did anyone setup WPA3 so far? Are the mentioned security flaws (at least to some extend) mitigated by now?
Somehow replacing hostapd by hostapd-openssl or wpad by wpad-openssl seems tricky because of dependencies - didn’t manage to install it yet 
I’ve tried WPA3 but none of the client devices I have support WPA3 yet. And one was unable to connect in mixed mode WPA3/WPA2. So I switched back to WPA2.