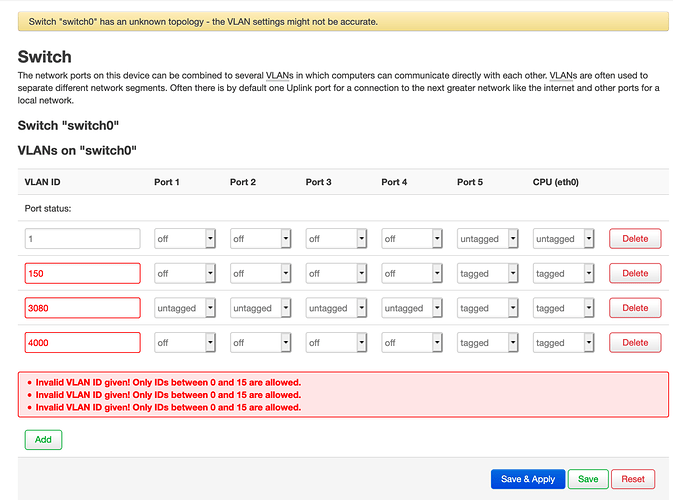
Well, I appreciate that it is supposed to work that way, but I just spent an entire day with it not functioning as documented in 4.0 (worked fine in 3.x). Here you can see the mess in LUCI:
Switch ports are not numbered correctly (not a big deal, other than it being an indication that the software is deeply confused), and it rejects the VLAN IDs. Digging into the LUCI code shows that it appears to first checks board.json for info, and failing that falls back to using swconfig to query the switch. If it can’t find either, it uses a default configuration (ports numbered 1-5, plus a CPU interface, and 4-bit VLANs) as shown. So what you’re seeing is basically LUCI throwing up its virtual hands and saying “OK, whatever, I’ll try to deal with this random situation.” If this happens to work in certain instances it’s still not the same as it functioning as intended.
Like many users with a reasonable background in Linux I consider LUCI to be a convenience and not a necessity, but switch configuration was not functioning as documented (by either Turris or OpenWRT) in /etc/config/network. Digging into the code, this also appears to center around the software’s belief that only 4-bit VLAN IDs are allowed on this switch (not true). So while the following lines will cause the LUCI interface to indicate the appearance of VLANs, they appear to do exactly nothing as far as switch configuration goes:
config switch
option name ‘switch0’
option reset ‘1’
option enable_vlan ‘1’
option enable_vlan4k ‘1’
config switch_vlan
option device ‘switch0’
option vlan ‘1’
option ports ‘4 5’
config switch_vlan
option device ‘switch0’
option vlan ‘150’
option ports ‘4t 5t’
config switch_vlan
option device ‘switch0’
option vlan ‘3080’
option ports ‘0 1 2 4t 5t’
config switch_vlan
option device ‘switch0’
option vlan ‘4000’
option ports ‘3 4t 5t’
Packets don’t flow as expected between ports, and none of the available command line tools that I’m aware of (I’m using “bridge” and “ip link”; there doesn’t appear to be a great replacement for swconfig yet) indicate that VLANs are configured on the ports. Indeed, it won’t even configure the existence of any LANx ports unless they’re explicitly added to a bridging configuration like so:
config interface ‘lan’
option type ‘bridge’
option proto ‘static’
option ipaddr ‘<>’
option netmask ‘<>’
option gateway ‘<>’
option broadcast ‘<>’
option dns ‘<>’
option ifname ‘eth2 lan3 lan4.4000’
This causes packets to flow as expected when used (I think!) in conjunction with the undocumented “enable_vlan4k” configuration option for the switch. The desired behavior is the creation of a software bridge between eth2 (separate WAN port) and vlan4000 on the switch cpu interface (eth0), with lan4 acting as an 802.1q trunk port with VLAN tag 4000 allowed and lan3 acting as a switch access port with the access (untagged) VLAN set to 4000. But from the shell prompt it really looks like everything is happening in software:
bridge -d vlan show dev lan3
port vlan ids
lan3 1 PVID Egress Untagged
I would expect to see:
bridge -d vlan show dev lan3
port vlan ids
lan3 4000 Egress Untagged
I can accomplish this manually by using these commands:
bridge -d vlan del vid 1 dev lan3 untagged
bridge -d vlan add vid 4000 dev lan3 untagged
So perhaps something is going on behind the scenes that is setting up the switch properly, but from the command line it really looks like this is not the case.