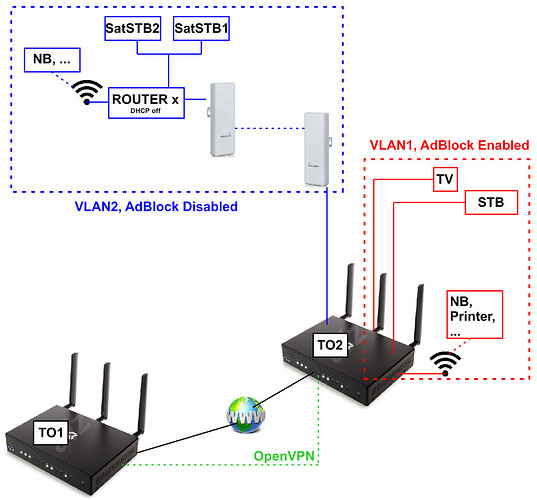
Hi, second Turris Omnia for my parents (TO2 on the image) is on the way, so it is time to ask some questions about my future plans for network. They are sharing their internet connection (FTTH) with neighbour. He lives in house about 100m away and connection is made via external Aps (802.11n - 5GHz). Now, they are all in one network and all devices are accessible etc.
First phase:
I would like to create two separate networks on TO2. One for my parents with AdBlock enabled (VLAN1) and VLAN2 for neighbour, without AdBlock (have been trying this at home, but without success). I don´t know if it will be possible then, to access and manage devices on that VLAN from the standard network.
Questions:
- How to set AdBlock properly, so that it will be active only on standard network and not on VLAN?
- How to access and manage devices on VLAN2 from VLAN1?
My actual network settings, when trying VLAN (where AdBlock is still active on both networks lan and lan_2) at home are:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd2a:c5a2:11ed::/48'
config interface 'lan'
option ifname 'eth0.1 eth2'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'lan_2'
option ifname 'eth0.3'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname '@wan'
option proto 'dhcpv6'
option noserverunicast '1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '5t 0 1 3'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '5t 2'
option vid '3'
config interface 'guest_turris'
option enabled '1'
option type 'bridge'
option ifname 'guest_turris_0 guest_turris_1'
option proto 'static'
option ipaddr '10.111.222.1'
option netmask '255.255.255.0'
option bridge_empty '1'
and DHCP
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option port '0'
option localservice '1'
option nonwildcard '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
config dhcp 'guest_turris'
option interface 'guest_turris'
option start '200'
option limit '50'
option leasetime '1h'
option ignore '0'
list dhcp_option '6,10.111.222.1'
config dhcp 'lan_2'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'lan_2'
list dhcp_option '6,192.168.3.1'
option force '1'
Second phase:
When everything from phase one will function properly, I would like to create Open VPN connection between TO1 (server) and TO2 (client) for occasional basic file sharing and to have possibility to access and manage devices on VLAN1 and VLAN2 on TO2. I am total noob in VPN stuff so I am sorry for possibly stupid questions.
Questions:
- Am I right that TO1 and TO2 must have different own ip addresses (e.g. TO1 – 192.168.1.1 and TO2 – 192.168.2.1)?
- My IP and parent´s IP change very occasionaly (both ipv4). Is it possible to set both omnia´s to send e-mail when IP is changed?
Other questions about VPN will probably come later…
Thank you for help. ![]()