It seems that the haas proxy has stopped operating properly? When I ssh to my IP address from an external connection, I’m prompted for login and password, but rather than getting the honeypot, the connection is closed immediately. Looking at haas.nic.cz, there haven’t been any ssh sessions for my router’s honeypot since 2018-08-16 06:32:39 Czech time.
anyone else seeing this?
I have updated to 3.10.4. 2 days ago (16.8.) and that were also my last records in haas …
haas process is between 60% and 100% of CPU load
@jork are you able to ssh to your router’s honeypot? If I try, the connection is closed immediately after I enter a username and password (fake ones of course). When haas works properly, you should get a simulated ssh session.
I sent @Pepe some logs to check out in regards to this as well.
same issue as you have. … session is closed immediately after I log in.
I have no records after 2009-07-04.
Running HP v1.9 on a linux server (not router) the same behaviour is observed and the HP log displaying
CRITICAL twisted ‘channel open failed, direct-tcpip is not allowed’
HP v1.7 worked fine but then issues started with v1.8 and are still there with v1.9.
IMHO there is something wrong with HP but the developers do not concur, after having reported issues.
@Pepe told me today this has been fixed on haas server side. I just tested and haas proxy is working properly for me again. Others may want to retest now. Thanks @Pepe
It seems that there is some imptovement but some issue are still lingering, e.g. log in with WinSCP does not work, at least that is with HP 1.9 on an Unbuntu server.
WinSCP stating
Error skipping startup message. Your shell is probably incompatible with the application (BASH is recommended).
The corresponding Haas Log
echo “WinSCP: this is end-of-file:0”
WinSCP is an SCP/SFTP client yes? I don’t think the haas proxy supports these, it only handles interactive shell sessions and not file transfers. I’ve tried those with PuTTY, Linux ssh and MacOS ssh and all of those work fine.
indeed
It used to work (version 1.7 did) but that may have changed in recent versions. At least the login over SCP would be expected to work (like for any other ssh client), actual file transfer/browsing is another matter though.
got it. I had never tried with an scp/sftp client before so wasn’t sure, but if you have observed it working before then it makes sense to raise the issue. was it possible to distinguish scp/sftp sessions at haas.nic.cz? It’s not obvious from the UI there.
I have no records on my HaaS since 4 July.
@WayOutWest the proxy is working well for me, so try some basic debugging?
-
Is the proxy running, eg ssh into the router and run
ps | grep haas -
is the proxy responding to requests, eg ssh into the router and do
ssh -p 2525 root@localhost, give a fake password, and see if you get the honeypot that nic.cz is running. The honeypot should look like below, you can type exit to exit the honeypot.The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.root@svr04:~# -
While on your home network, find your IP address using a site such as https://www.whatismyip.com/ Then, connect to a network other than your home network and try to ssh to your router as an attacker would, eg
ssh root@your_ip_addressAgain, give a fake password. You should get the honeypot like the above.
There’s likely something going wrong at one of these 3 points.
Many thanks tonyquan. I will try this tomorrow. Almost 1am here–off to bed! Thanks once again!
login as: root
root@192.168.15.1's password:
BusyBox v1.25.1 (2018-08-14 17:16:55 CEST) built-in shell (ash)
_______ _ _ _____ _____ _____ _____
|__ __|| | | || __ \ | __ \ |_ _| / ____|
| | | | | || |__) || |__) | | | | (___
| | | | | || _ / | _ / | | \___ \
| | | |__| || | \ \ | | \ \ _| |_ ____) |
|_| \____/ |_| \_\|_| \_\|_____||_____/
root@turris:~# ps | grep haas
336 root 1116 S grep haas
7379 root 26712 S /usr/bin/python2.7 -m haas_proxy -n --pidfile=/tmp/h
root@turris:~# ssh -p 2525 root@localhost
The authenticity of host '[localhost]:2525 ([127.0.0.1]:2525)' can't be established.
RSA key fingerprint is XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
Warning: Permanently added '[localhost]:2525' (RSA) to the list of known hosts.
root@localhost's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
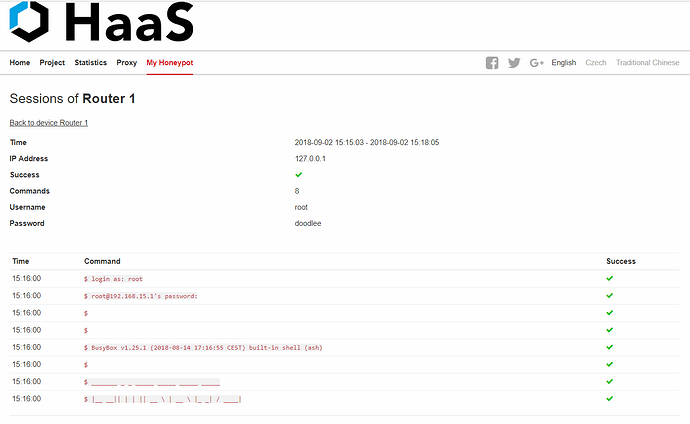
root@svr04:This just turned up in my Honeypot logs
What was the result of test 3 of the ones I suggested (try to ssh to your home IP address from a network other than your home network) From what you’ve shown the problem is likely there, something is blocking external ssh attempts from reaching the router.