Hi,
I just tried to setup 802.11r on my Omnia using luci’s gui:
Background information I got from thread1 and thread2 and I tested my core devices (Apple and Samsung) successfully in a similar surrounding with 3 floors each having a OpenWRT 18.06.2 running router/ap with enabled 802.11r.
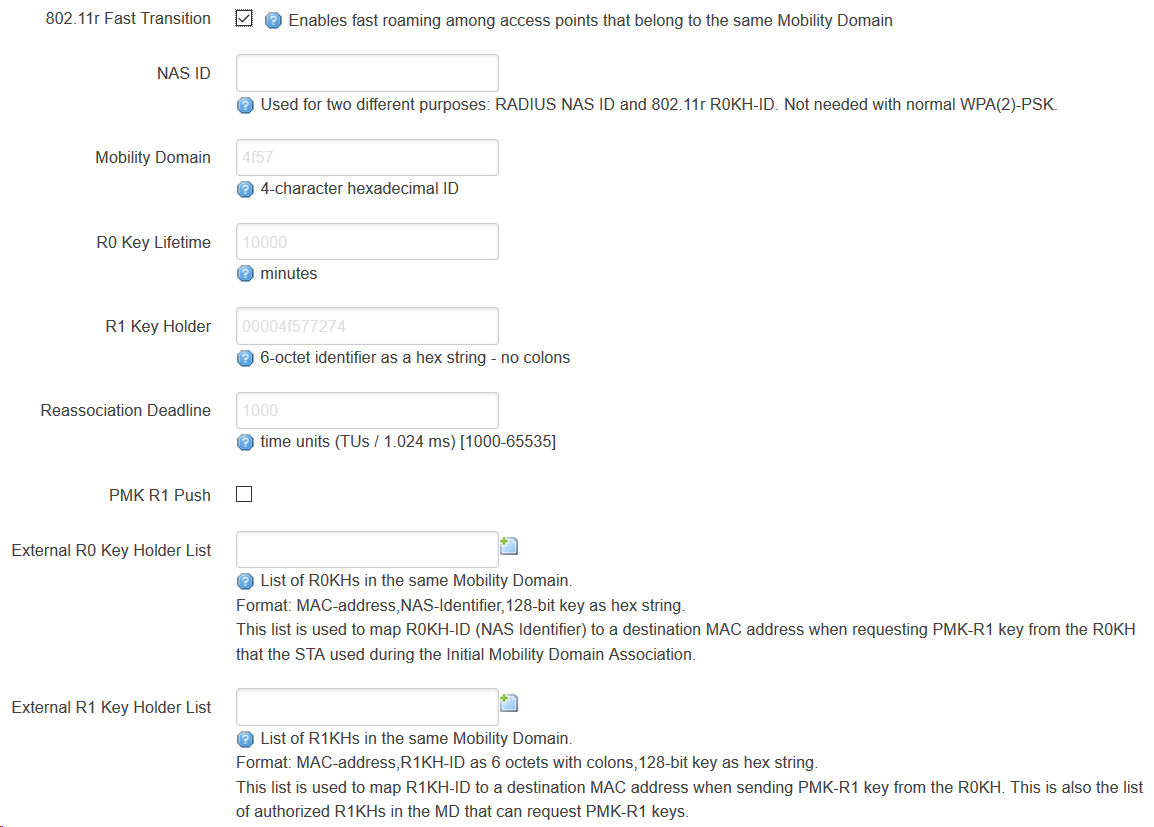
Comparing the options of the TO (above) to those of my ap (linksys WRT1900AC, wpad (full) installed, below) shows the options of TO are lacking functionality:
The above shown marked options would leave the following additional wireless configuration lines for the chosen ssid on my TO:
option ieee80211r '1'
option ieee80211w '0'
but unfortunatelly after restarting the network this radio device would never come up again (rebooting doesn’t help, it’s all the same for the 2,4GHz- and the 5GHz-wifi-cards)…
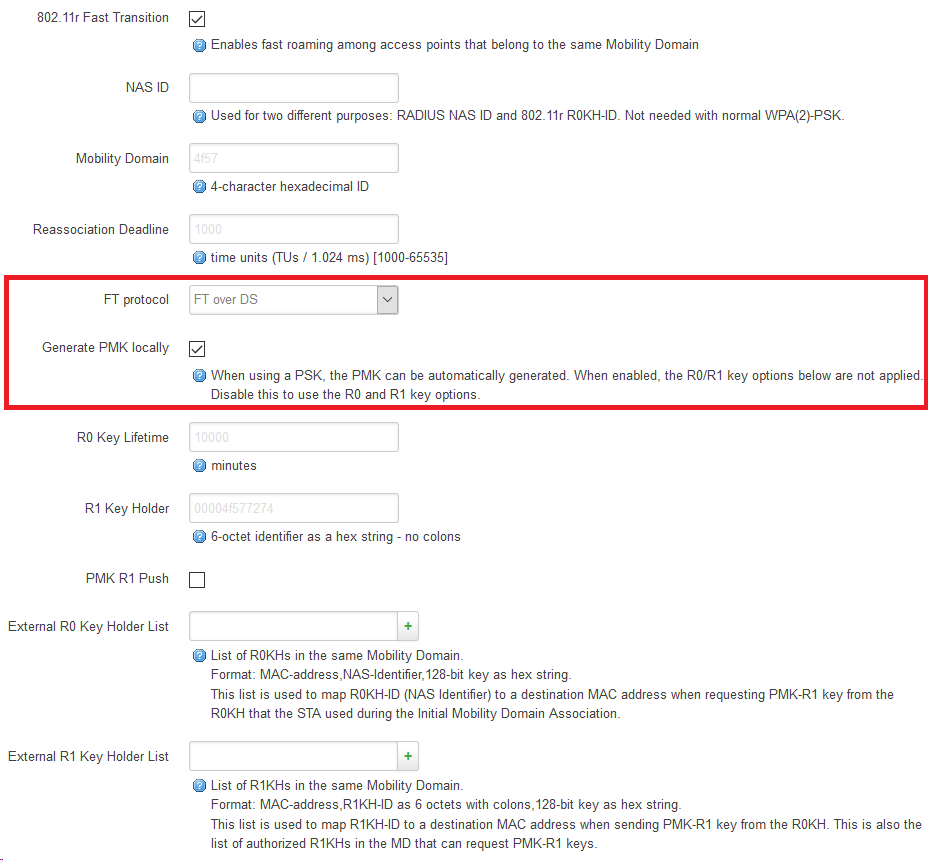
At my ap there’s more information stored to the ssid:
option ieee80211r '1'
option ft_over_ds '1'
option ft_psk_generate_local '1'
and… the radio devices will come up without any problem.
So my question is: Do you other guys also have the same problem with 802.11r on your TO?
The only modification I did to my TO was swapping the small 2,4GHz-card for a WLE1216V5-20 [mPCIe-slot 0; running on 5GHz] and configuring the WLE900VX [mPCIe-slot 1] to run on 2,4GHz.
But I believe this problem to not be related to my hardware but to the outdated wpad package: my linksys WRT1900AC runs wpad 2018-05-21-62566bc2-5 whereas the TO has only version 2016-12-19-8 available. ![]()
ps: I did this because of the problem that several devices keep beeing connected to the TO as if clued to its ssids (whereas the same devices do a perfect job in the abovementioned surrounding). It’s really annoying ![]()
Unfortunatelly I was forced to have only ca. 2,5 meters in between the TO’s and the ap’s antennas in the core of my rented flat. So in this core area roaming is a problem - just contrary to the edge regions of my flat, where there is only one (TO or ap) wifi reachable…