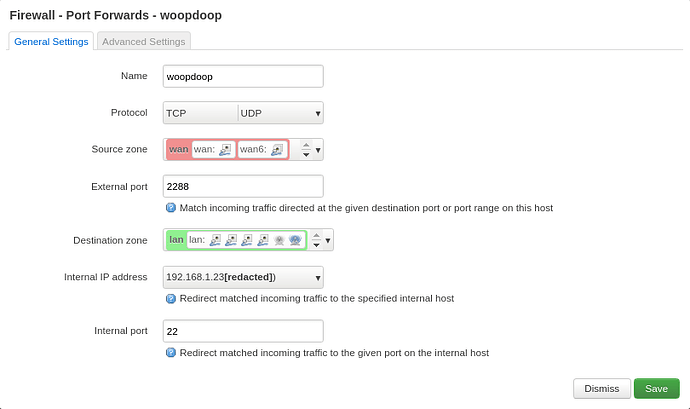
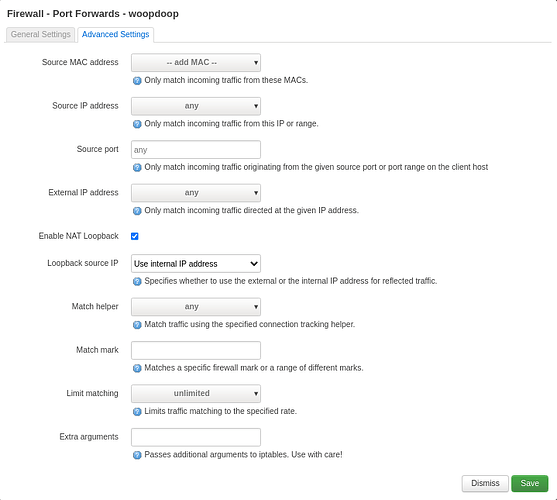
Thanks a lot for your reply. Finally had the time to do this, and here are the results. It seems that my Omnia is seeing something when I try to connect via SSH, but not sure what.
Assume 93.184.216.34 is where I’m connecting from.
root@rawter:~# tcpdump -i eth2 tcp port 2288
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth2, link-type EN10MB (Ethernet), capture size 262144 bytes
19:57:57.760168 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879415677 ecr 0,nop,wscale 7], length 0
19:57:58.781224 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879416700 ecr 0,nop,wscale 7], length 0
19:58:00.838735 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879418748 ecr 0,nop,wscale 7], length 0
19:58:04.863293 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879422780 ecr 0,nop,wscale 7], length 0
19:58:13.371790 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879431292 ecr 0,nop,wscale 7], length 0
19:58:29.760700 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879447676 ecr 0,nop,wscale 7], length 0
19:59:02.012349 IP 93.184.216.34.55098 > redacted-ip-example.org.2288: Flags [S], seq 1459565480, win 64860, options [mss 1380,sackOK,TS val 1879479932 ecr 0,nop,wscale 7], length 0
^C
7 packets captured
7 packets received by filter
0 packets dropped by kernel
###
root@rawter:~# tcpdump -i br-lan host 192.168.1.23
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on br-lan, link-type EN10MB (Ethernet), capture size 262144 bytes
20:04:58.795296 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [P.], seq 2461020285:2461020361, ack 3741546364, win 501, options [nop,nop,TS val 384295157 ecr 81564835], length 76
20:04:58.795782 IP 192.168.1.23.22 > 192.168.1.5.60394: Flags [P.], seq 1:133, ack 76, win 1026, options [nop,nop,TS val 81566845 ecr 384295157], length 132
20:04:58.796662 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [.], ack 133, win 500, options [nop,nop,TS val 384295158 ecr 81566845], length 0
# ... Lots of similar seq/ack log entries omitted.
20:05:11.006489 IP 93.184.216.34.55304 > 192.168.1.23.22: Flags [S], seq 3705302969, win 64860, options [mss 1380,sackOK,TS val 1879848919 ecr 0,nop,wscale 7], length 0
20:05:11.006758 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:12.062612 IP 93.184.216.34.55304 > 192.168.1.23.22: Flags [S], seq 3705302969, win 64860, options [mss 1380,sackOK,TS val 1879849980 ecr 0,nop,wscale 7], length 0
20:05:12.062775 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
# ... Lots of similar seq/ack log entries omitted.
20:05:14.108864 IP 93.184.216.34.55304 > 192.168.1.23.22: Flags [S], seq 3705302969, win 64860, options [mss 1380,sackOK,TS val 1879852028 ecr 0,nop,wscale 7], length 0
20:05:14.109027 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:14.896919 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [P.], seq 660:736, ack 1133, win 501, options [nop,nop,TS val 384311258 ecr 81580933], length 76
20:05:14.897467 IP 192.168.1.23.22 > 192.168.1.5.60394: Flags [P.], seq 1133:1265, ack 736, win 1026, options [nop,nop,TS val 81582946 ecr 384311258], length 132
20:05:14.898761 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [.], ack 1265, win 500, options [nop,nop,TS val 384311260 ecr 81582946], length 0
20:05:16.049207 ARP, Request who-has 192.168.1.23 tell 192.168.1.1, length 28
20:05:16.049471 ARP, Reply 192.168.1.23 is-at [redacted-mac-address] (oui Unknown), length 46
20:05:16.909122 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [P.], seq 736:812, ack 1265, win 501, options [nop,nop,TS val 384313271 ecr 81582946], length 76
20:05:16.909633 IP 192.168.1.23.22 > 192.168.1.5.60394: Flags [P.], seq 1265:1397, ack 812, win 1026, options [nop,nop,TS val 81584958 ecr 384313271], length 132
20:05:16.910341 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [.], ack 1397, win 500, options [nop,nop,TS val 384313272 ecr 81584958], length 0
20:05:16.931795 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:18.139573 IP 93.184.216.34.55304 > 192.168.1.23.22: Flags [S], seq 3705302969, win 64860, options [mss 1380,sackOK,TS val 1879856060 ecr 0,nop,wscale 7], length 0
20:05:18.139861 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
# ... Lots of similar seq/ack log entries omitted.
20:05:21.148834 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:21.995809 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:22.952229 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [P.], seq 964:1040, ack 1661, win 501, options [nop,nop,TS val 384319314 ecr 81588985], length 76
20:05:22.952767 IP 192.168.1.23.22 > 192.168.1.5.60394: Flags [P.], seq 1661:1793, ack 1040, win 1026, options [nop,nop,TS val 81591001 ecr 384319314], length 132
20:05:22.954104 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [.], ack 1793, win 500, options [nop,nop,TS val 384319315 ecr 81591001], length 0
20:05:24.412143 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:24.966038 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [P.], seq 1040:1116, ack 1793, win 501, options [nop,nop,TS val 384321328 ecr 81591001], length 76
20:05:24.966590 IP 192.168.1.23.22 > 192.168.1.5.60394: Flags [P.], seq 1793:1925, ack 1116, win 1026, options [nop,nop,TS val 81593015 ecr 384321328], length 132
20:05:24.967650 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [.], ack 1925, win 500, options [nop,nop,TS val 384321329 ecr 81593015], length 0
20:05:26.527025 IP 93.184.216.34.55304 > 192.168.1.23.22: Flags [S], seq 3705302969, win 64860, options [mss 1380,sackOK,TS val 1879864444 ecr 0,nop,wscale 7], length 0
20:05:26.527303 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
20:05:26.859673 IP 192.168.1.23.5353 > 224.0.0.251.5353: 0*- [0q] 1/0/1 (Cache flush) A 192.168.1.23 (55)
20:05:26.975487 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [P.], seq 1116:1192, ack 1925, win 501, options [nop,nop,TS val 384323337 ecr 81593015], length 76
20:05:26.976042 IP 192.168.1.23.22 > 192.168.1.5.60394: Flags [P.], seq 1925:2057, ack 1192, win 1026, options [nop,nop,TS val 81595024 ecr 384323337], length 132
20:05:26.976878 IP 192.168.1.5.60394 > 192.168.1.23.22: Flags [.], ack 2057, win 500, options [nop,nop,TS val 384323338 ecr 81595024], length 0
20:05:27.698264 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
# ... Lots of similar seq/ack log entries omitted.
20:05:42.909274 ARP, Request who-has 192.168.1.254 tell 192.168.1.23, length 46
# ... Lots of similar seq/ack log entries omitted.
20:05:47.959207 ARP, Request who-has 192.168.1.23 tell 192.168.1.1, length 28
20:05:47.959433 ARP, Reply 192.168.1.23 is-at [redacted-mac-address] (oui Unknown), length 46
# ... Lots of similar seq/ack log entries omitted.
^C
112 packets captured
113 packets received by filter
0 packets dropped by kernel